If you have a use case to exclude or include certain devices from a conditional access policy, Microsoft gives us the option to “filter for devices” when creating or editing a policy. For example, you can exclude all Dell devices from a policy. In this demonstration, I have a conditional access policy to block sign-ins from non-compliant devices. I will make a filter to exclude a specific non-compliant device from this policy. We will test the policy and look at the sign-in logs to see what happens.
Before I begin, I want to take a minute to show which properties we have available when creating a device filter for a conditional access policy. The drop down contains a variety of options, including custom extension attributes (if they are set). See the list below:
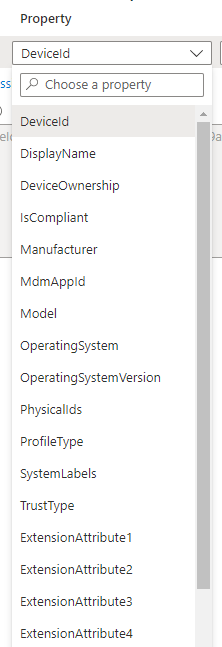
If you are not certain what the value is for one of those fields on your target device(s), we can use the graph explorer and pull the device properties. Navigate to Graph Explorer | Try Microsoft Graph APIs – Microsoft Graph. Once you’re there, you can pull the properties of all your devices, or you can specify one device by the device ObjectID. Take a look at the screen shots below. The top screenshot shows where you can retrieve a device ObjectID in AzureAD. The next screenshot shows the graph explorer and how we pull device details.
https://graph.microsoft.com/v1.0/devices <- Pulls all device details
https://graph.microsoft.com/v1.0/devices/6c1b15af-6126-4b94-994c-6f7969f4ad46 <- Object ID added to only pull details for specific device.
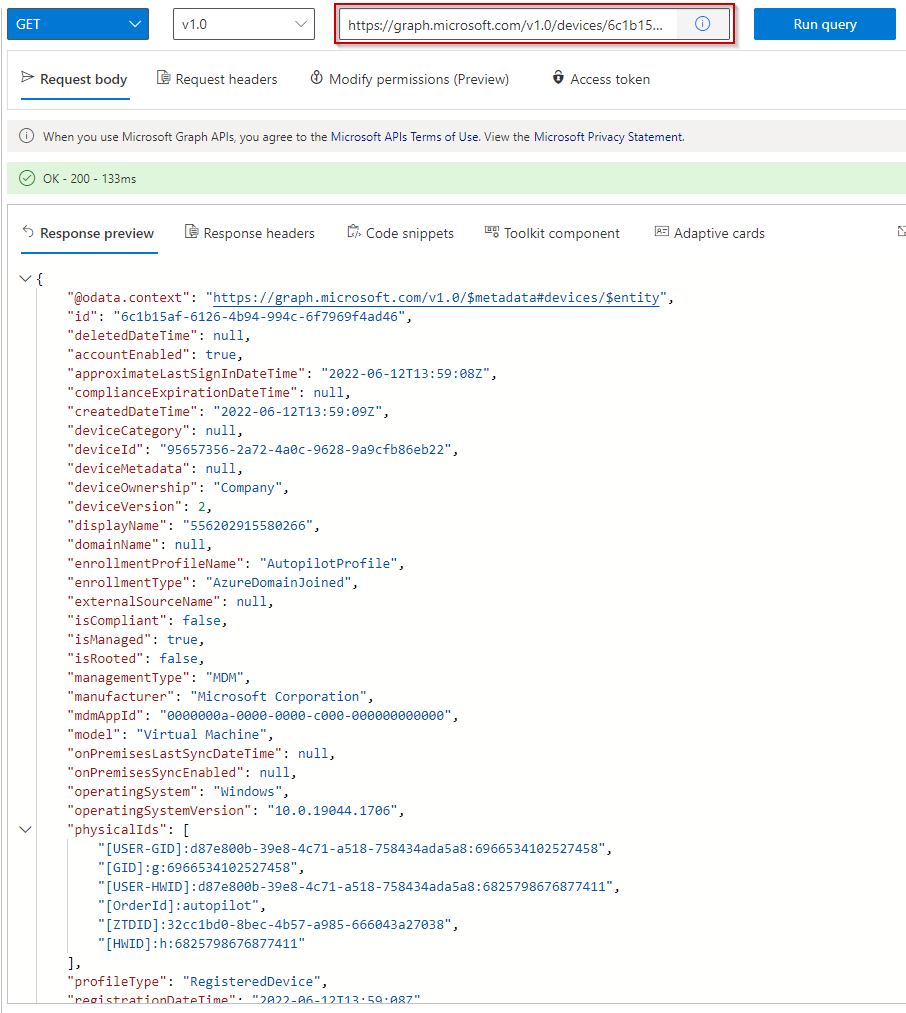
I highlighted fields in the below we can use for making our device filter in a conditional access policy. In this demonstration, we will use the deviceID (which is also easily available in the device properties of AzureAD).
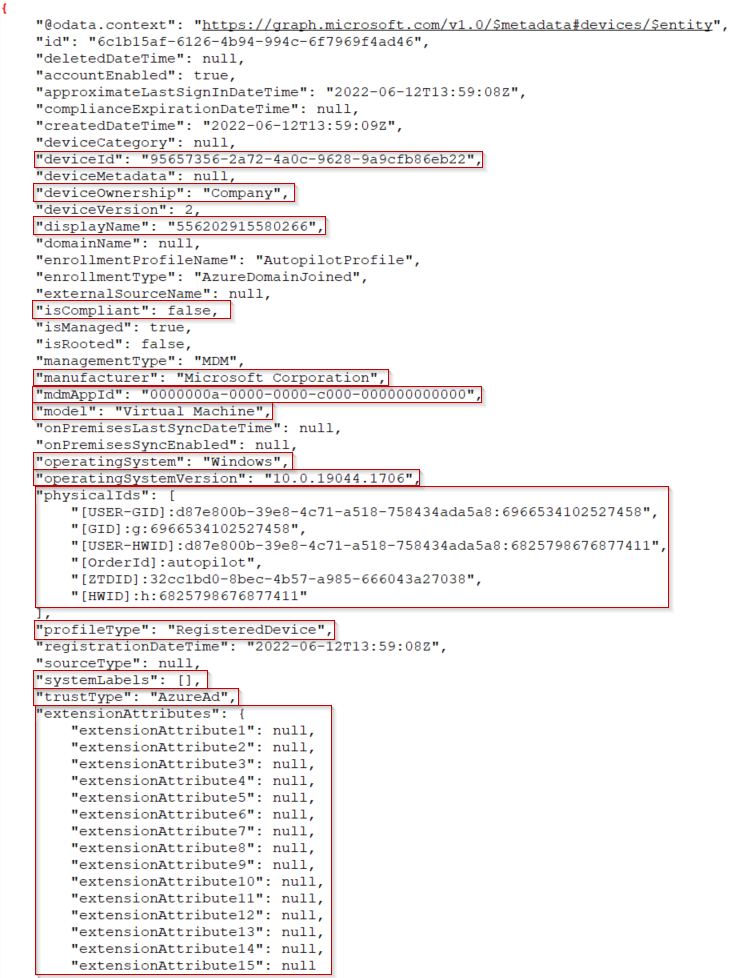
Now that we have identified our property and value for our device filter, we can edit our conditional access policy to exclude this device. Here is a policy to block non-compliant devices. Open your conditional access policy, and under conditions, select filter for devices.
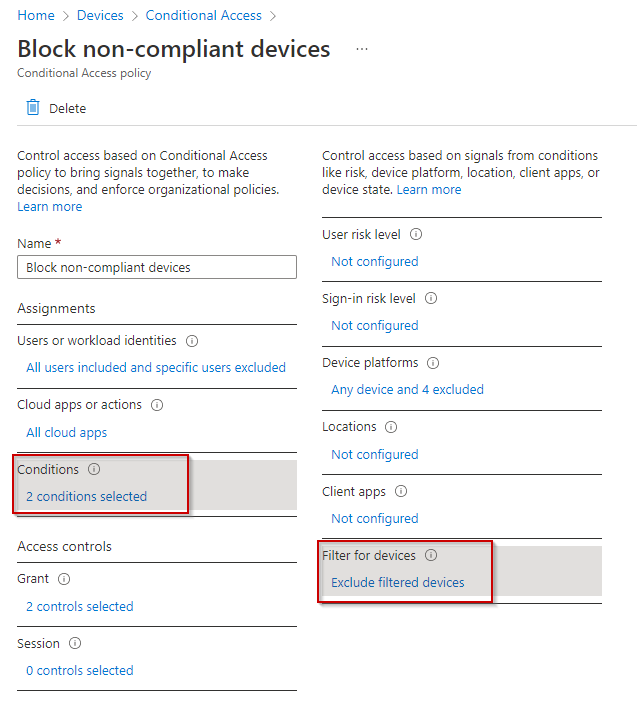
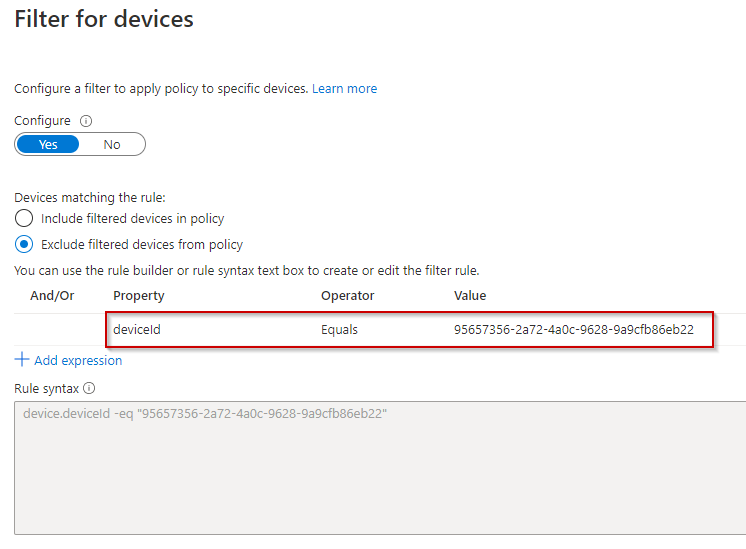
Toggle configure to Yes, select exclude filtered devices from policy, and edit the fields. As previously mentioned, in this example we are using deviceID. If this is a new policy and you want to test prior to putting into production, I strongly suggest putting the policy in Report-Only mode and doing some testing. If the policy is already on and in production, double check your policy settings and user exclusions, and click Save.
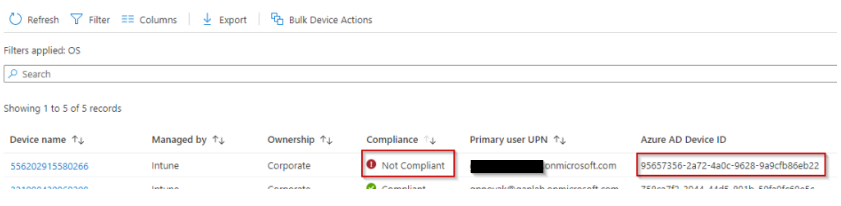
Here is our target device in endpoint manager showing the matching deviceID and not compliant:
If I try signing in on that device with a standard user, the sign-in is allowed. If we look at the sign-in logs, we can see the details on the conditional access policy. If you don’t know how to get to the sign-in logs, select the user signing in from the users blade in endpoint manager. Select Sign-in logs under activity. This will filter the sign-ins only for that user. Locate the sign-in log entry and select it. Go to the conditional access tab, find your conditional access policy, click the three dots and select show details:
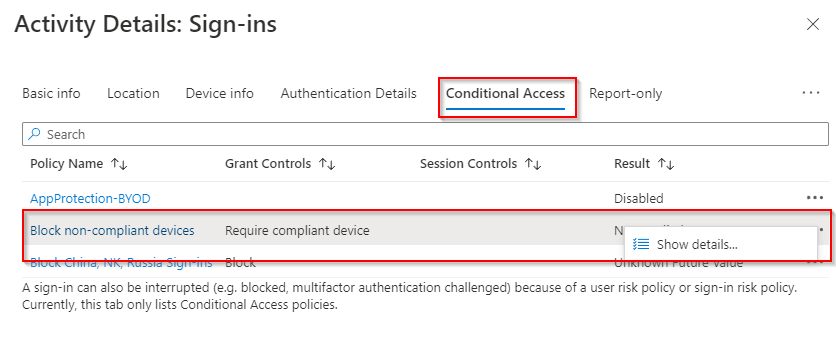
Here are the conditional access details for the user sign-in. We can see below that the policy result was “not applied”, and our device ID shows as a match, which allows me to sign in on the non-compliant device.
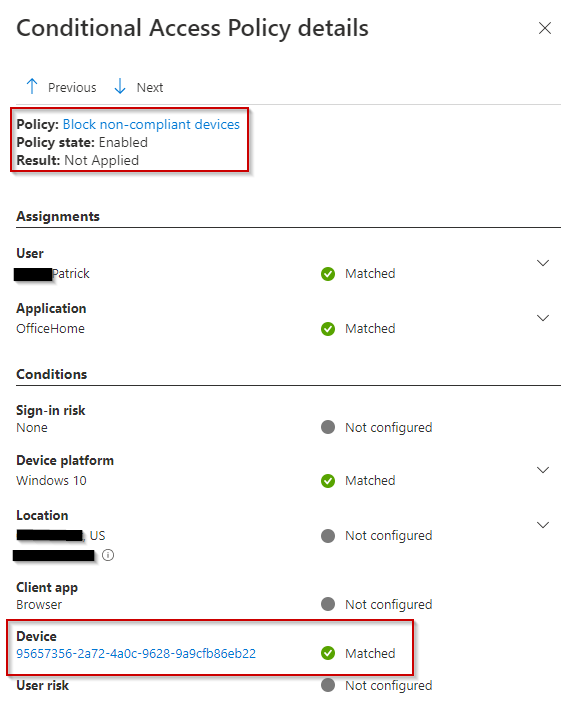
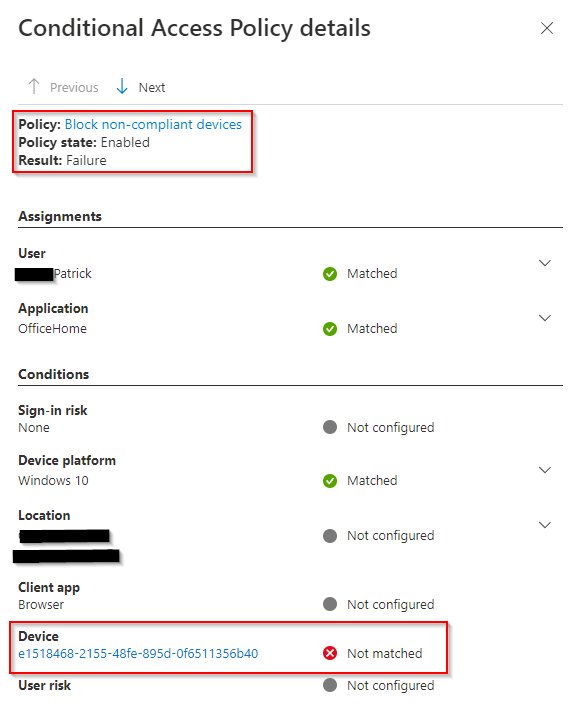
If I try signing in with the same account on a different non-compliant device, I am blocked. You can see in the screenshot the conditional access result of Failed, and the device ID doesn’t match any exclusions.
Additional details and Microsoft documentation on this topic can be found here: Filter for devices as a condition in Conditional Access policy – Azure Active Directory – Microsoft Entra | Microsoft Docs.

Pingback: Endpoint Manager Newsletter – 17th June 2022 – Andrew Taylor