Getting devices registered in autopilot can be a pain if they are already in production. I wrote a post last month about uploading hardware hashes to blob storage (or a network share) and then merging the CSV hashes into a single file for upload. However, I recently discovered the Get-WindowsAutoPilotInfo script can authenticate to your target tenant using an app registration. So, I started doing some testing and created a new AzureAD app registration. Next, I did some reading on the Graph application permissions for Intune. After some trial and error, and some testing, I found I needed the following Graph API permissions assigned to my app to enroll a device and assign a grouptag (this may be different if you use other switches):
- DeviceManagementApps.ReadWrite.All
- DeviceManagementConfiguration.ReadWrite.All
- DeviceManagementManagedDevices.ReadWrite.All
- DeviceManagementServiceConfig.ReadWrite.All
Since I’ll be reusing this method, I wanted to script as much of this as possible. I did some research and the whole app registrations can be created through PowerShell. The Microsoft resources I used to create this script are below for reference:
- https://docs.microsoft.com/en-us/powershell/module/az.resources/new-azadapplication?view=azps-8.1.0&viewFallbackFrom=azps-7.4.0
- https://docs.microsoft.com/en-us/powershell/module/az.resources/add-azadapppermission?view=azps-8.1.0&viewFallbackFrom=azps-7.4.0
- https://docs.microsoft.com/en-us/graph/permissions-reference
The app registration script
The script does several things to create the app registration and can be adjusted for your environment as needed. Make sure to use the graph permission reference link above if you want to add permissions to your application. Also, since this will likely only be used for a short time, I have the app secret set to expire 10 days after the app is created. If you want this longer/shorter, adjust accordingly. Script is available on github and a description of how it works is below:
- The script prompts the user to sign-in to the target Azure and AzureAD tenant
- Prompts to name the application
- Assigns the graph API application permissions
- Sets the expiration for the secret for 10 days after its created (can be adjusted)
- Auto-launches a browser to give admin consent for the permissions (some kudos to a friend who helped me with this part)
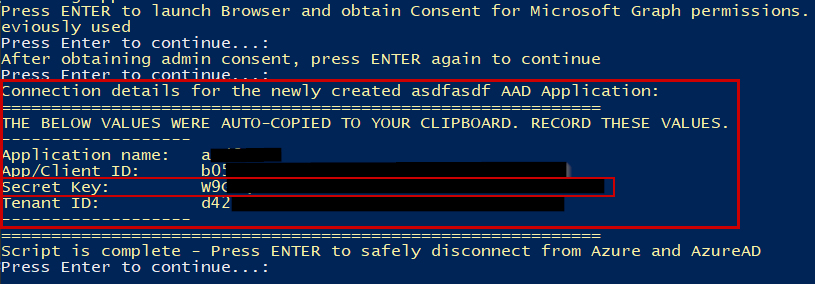
- Outputs the Application name, AppID, Secret Key, and Tenant ID, and auto copies those values to the clipboard
- Make sure you save the secret key for the app registration. You won’t be able to retrieve it again, but you can always make another one if needed.
- Disconnects from Azure and AzureAD.
Here is the script in action:
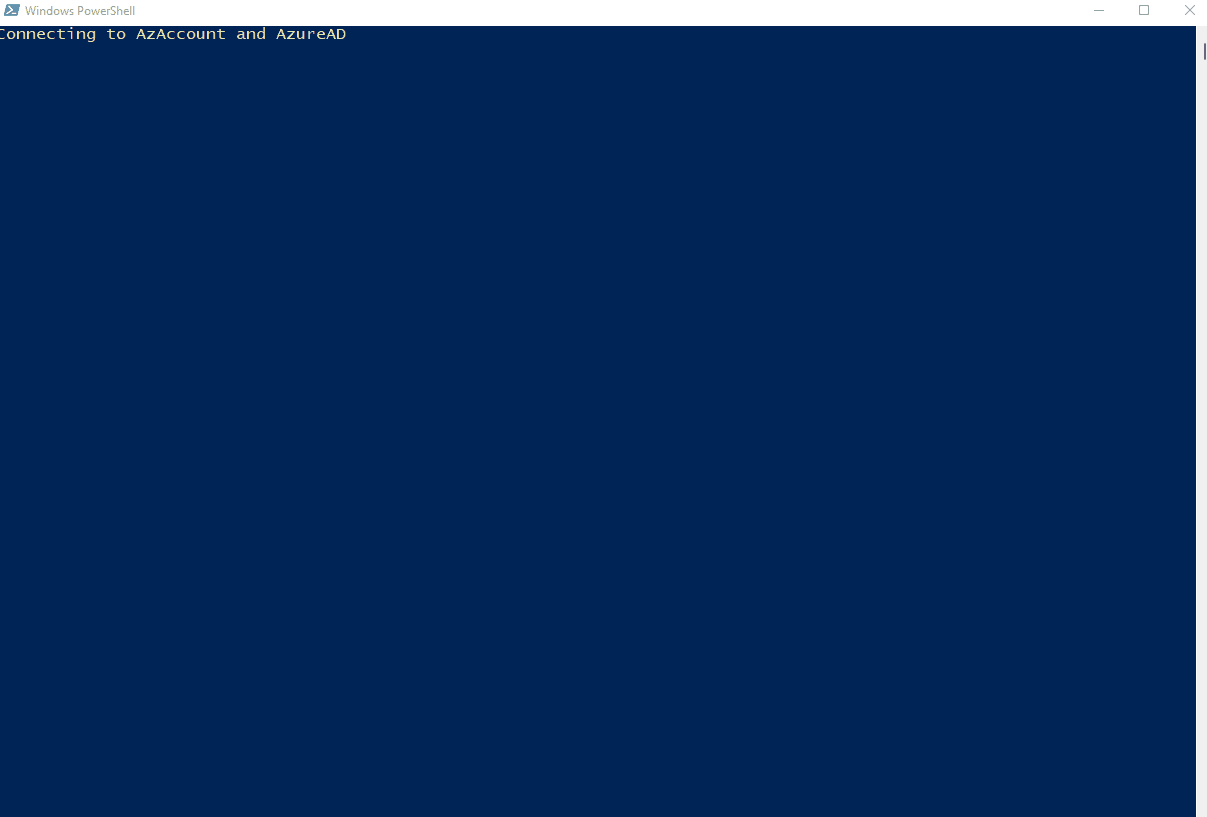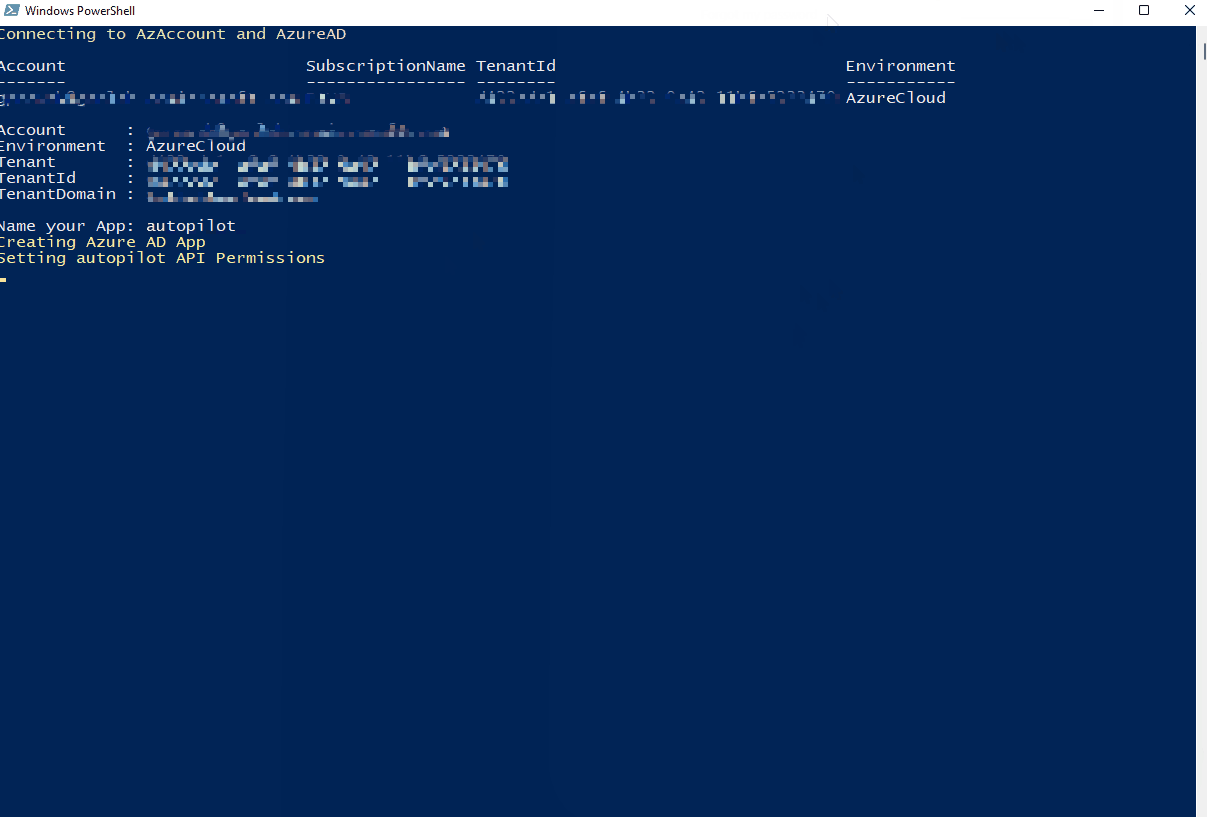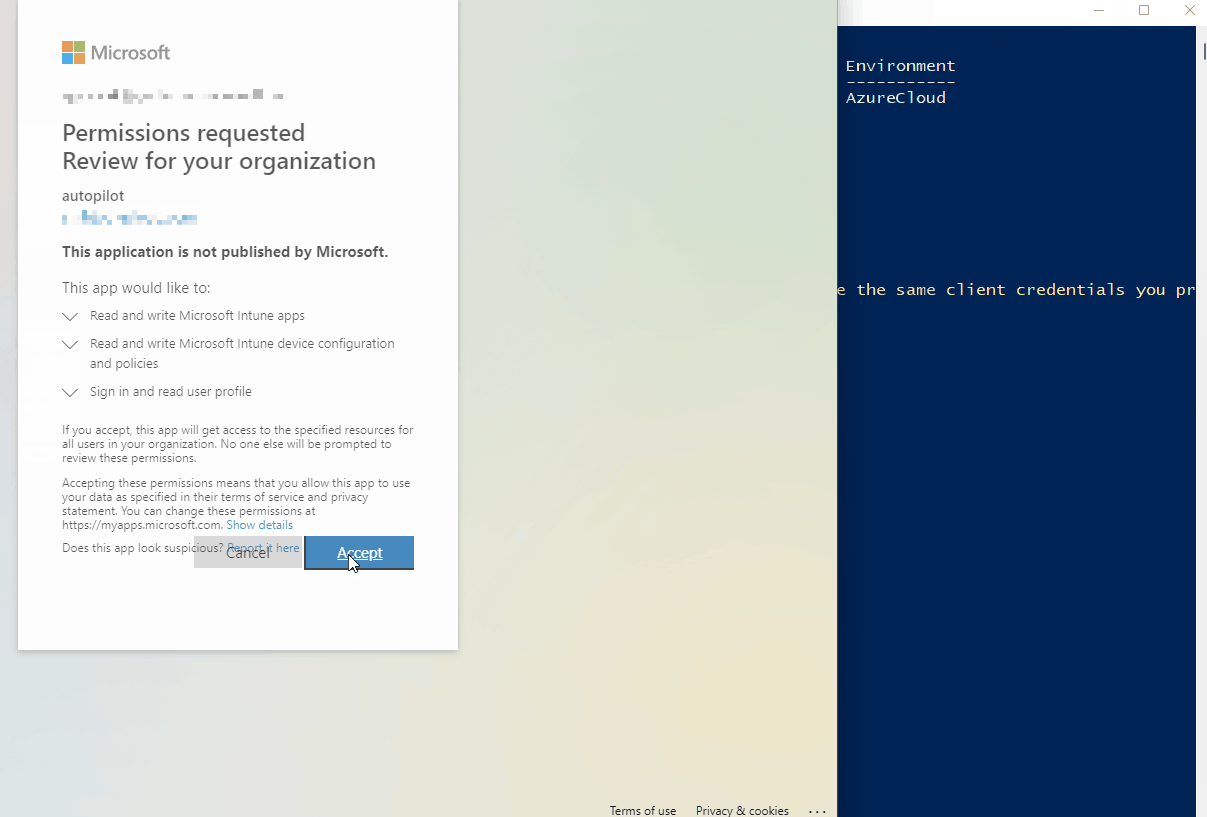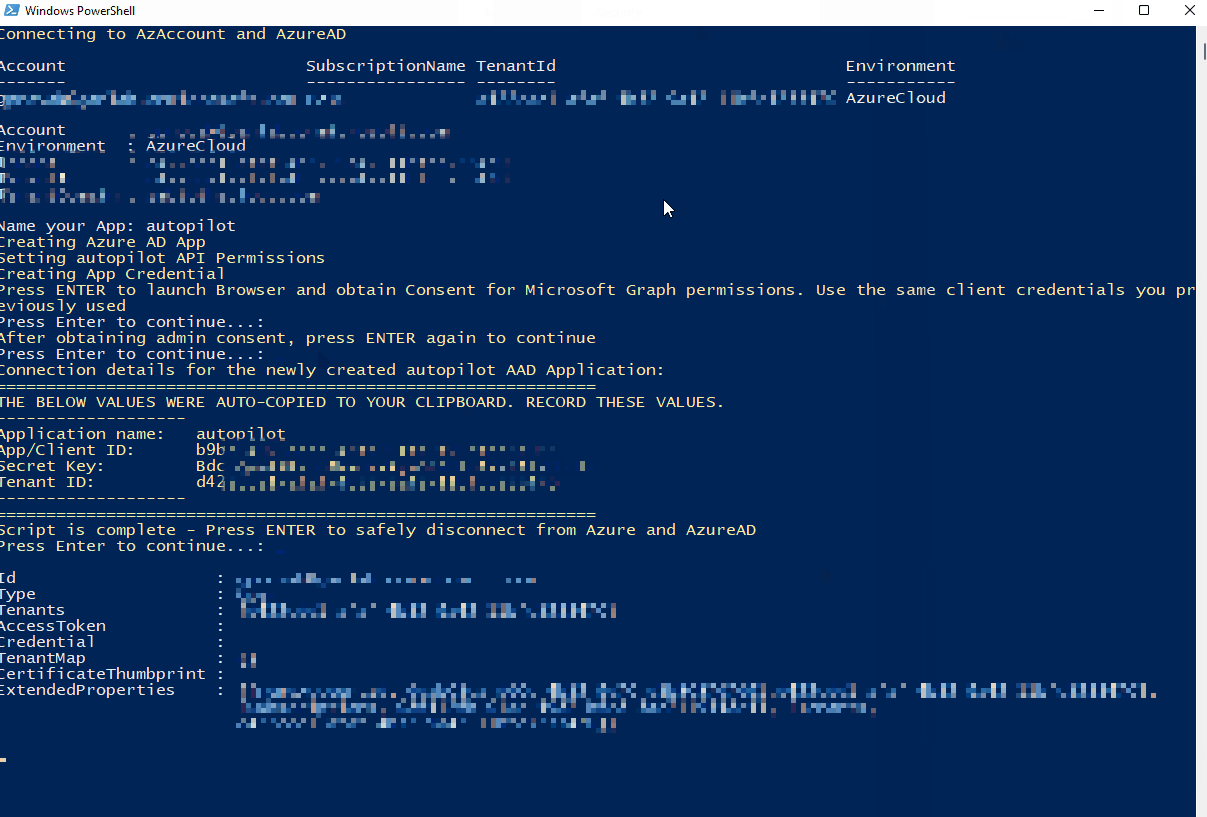
As previously mentioned, make sure you paste or record the values output on the screen (shown below). You can easily retrieve the App ID and Tenant ID, but the secret key is only viewable once. You will have to create a new one if you lose the value:
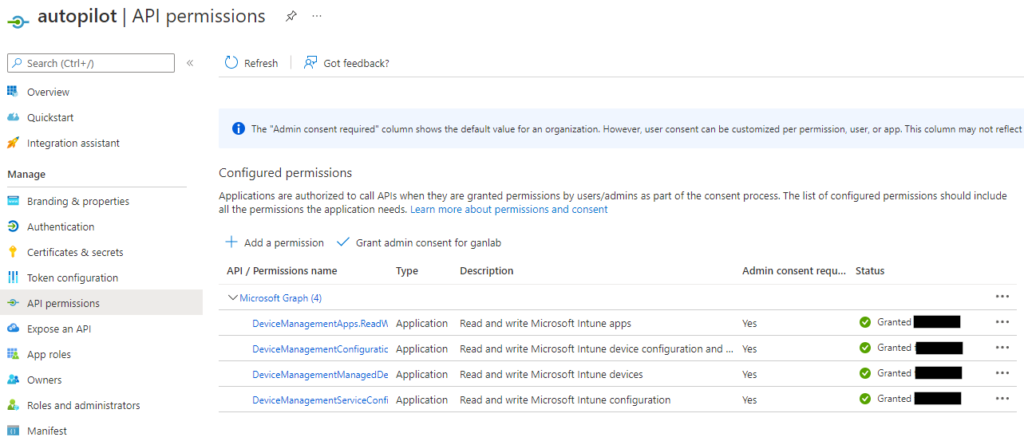
Here is our new app and API permissions showing in the GUI:
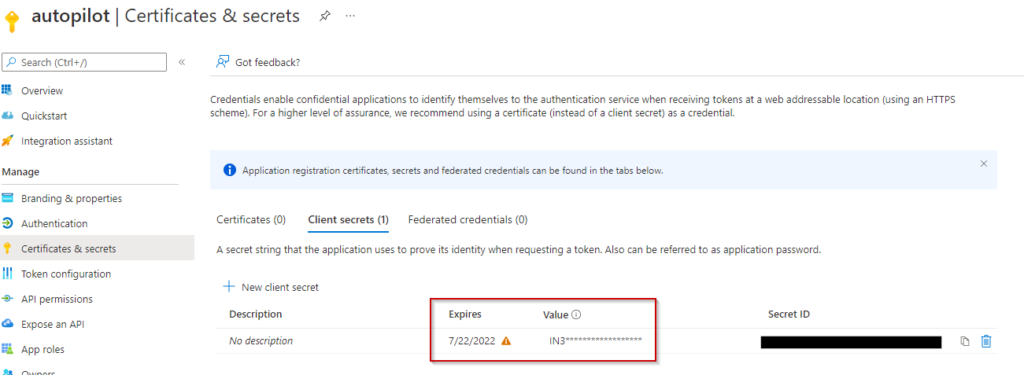
And screenshot showing the secret and its expiration:
Autopilot register using the app registration
Next, we will use this app to authenticate and register a device in autopilot. Since we are using the app for authentication, the device is imported at the time the script. There is no prompt for a user to authenticate and no CSV hardware hash files to manually upload. This can be silently pushed out with an RMM, or manually executed on workstations. The script is rather simple. Add your grouptag, and specify the values for the app we registered earlier:
#Variables
$TenantID = " xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
$AppID = " xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
$AppSecret = "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
$GroupTag = "autopilot"
#RegisterDevice
Set-ExecutionPolicy Unrestricted -Force
Install-PackageProvider NuGet -Force -ErrorAction SilentlyContinue
Install-Script Get-WindowsAutoPilotInfo -Force
Get-WindowsAutoPilotInfo -Online -TenantId $TenantID -AppID $AppID -AppSecret $AppSecret -GroupTag $GroupTagWhen we execute on a target machine manually, you can see the connection to Azure is made using app-based authentication via our app registration we previously created:
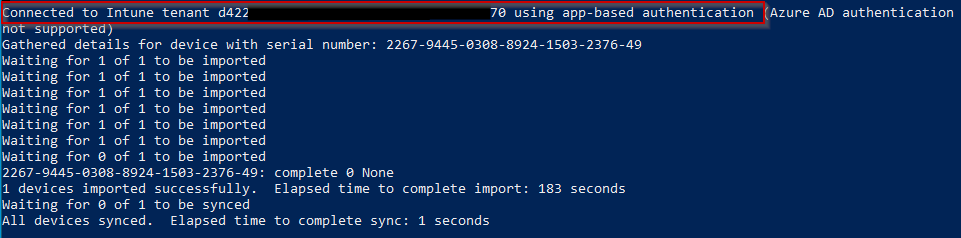
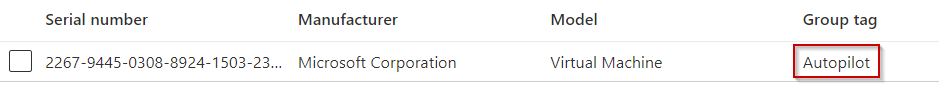
If we look at our autopilot devices, we can see the device was enrolled in autopilot with our specified grouptag from the script: