Conditional Access is constantly evolving and adding new features. One of the newer features is conditional access for workload identities. This allows us to secure service principals for our app registrations. At the moment, this is limited to two conditions – service principal risk and/or Locations. Personally, I’d like to see grant controls for compliant devices as well, but more features will likely be added in the future. For more detailed info, visit this MS learn page – Azure Active Directory Conditional Access for workload identities – Microsoft Entra | Microsoft Learn. A few important things to take away from the MS Learn:
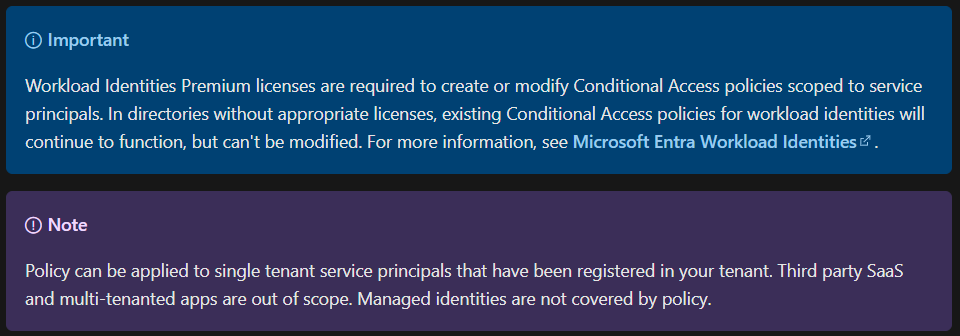
Before we get started, we need to make sure we have the appropriate license. We need Workload Identity Premium licenses for each service principal we want to protect with conditional access. At the time of writing, these are $3 per month per workload identity. We can also trial the license for 90 days. You can activate the trial from this link – Activate – Microsoft Entra admin center
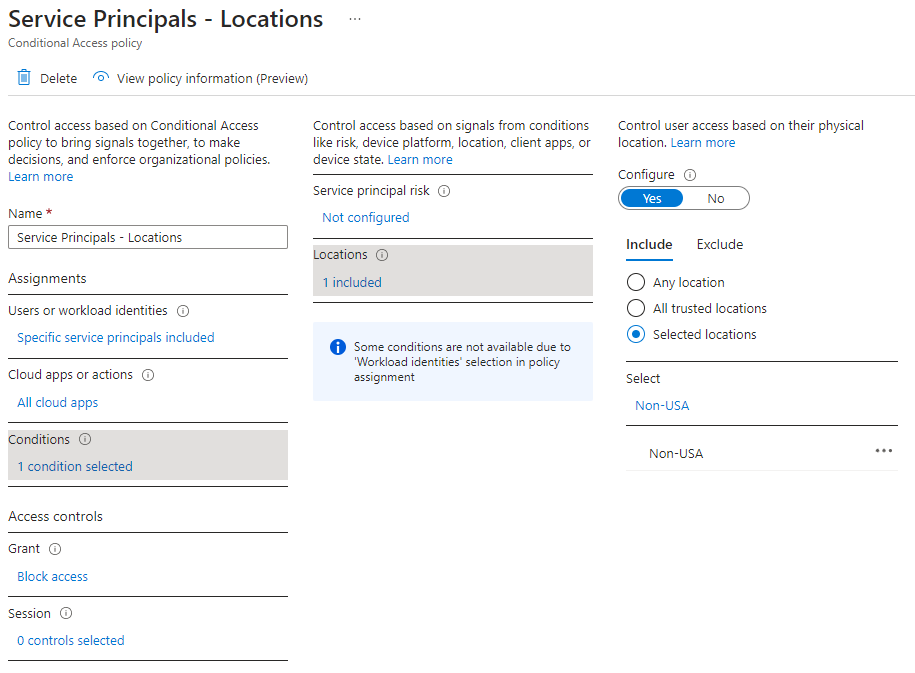
Once you have your licenses, you’ll see “workload identities” under the assignments portion of a conditional access policy. This is where instead of selecting a user or group of users, we can select a specific service principal:
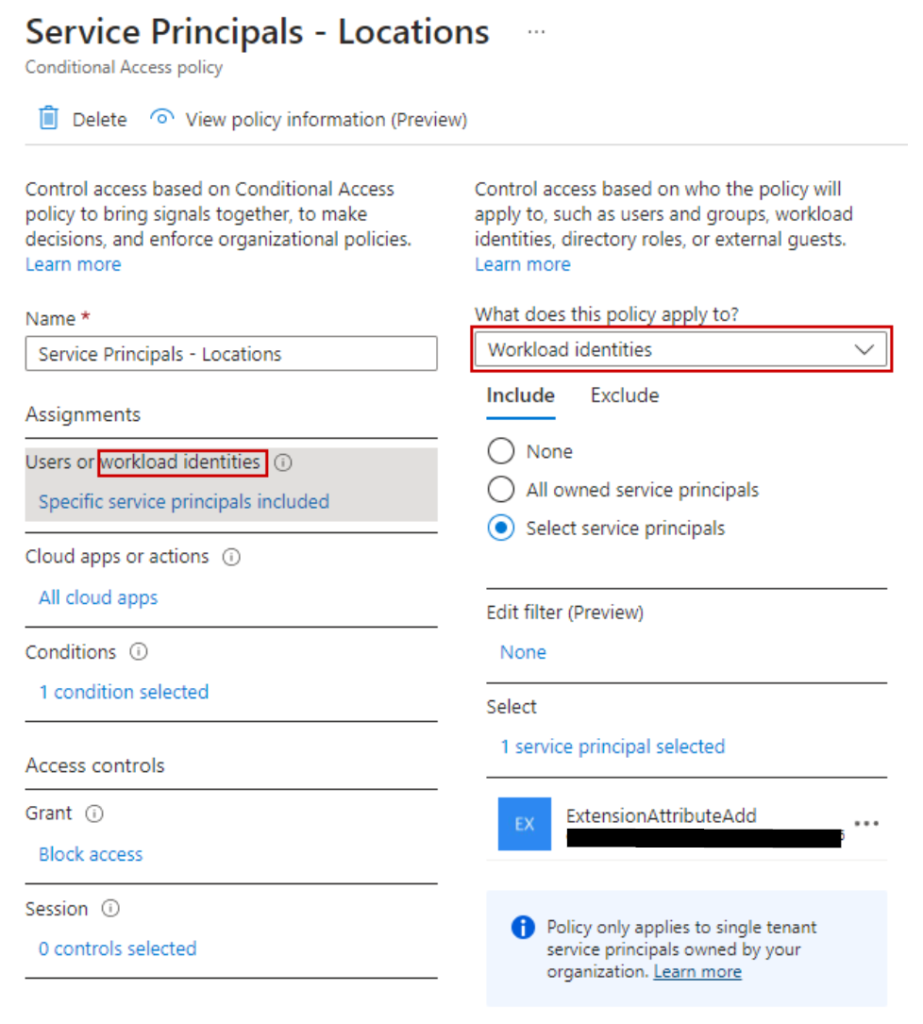
Next, we can set our conditions. It’s important to note that for location, we can only use the block control. So, I made a location that includes all non-USA-based IPs. This allowed me to test the CA policy using a VPN.
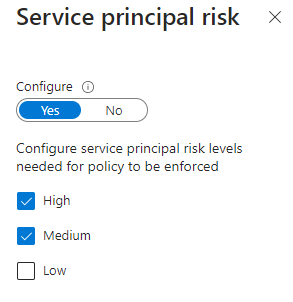
We can also use service principal risk. For details on how risk is detected for workload identities, visit this link – Securing workload identities with Azure AD Identity Protection – Microsoft Entra | Microsoft Learn.
We can use the what-if tool just like user based conditional access policies. Here you can see a what-if tested against my service principal risk conditional access policy:

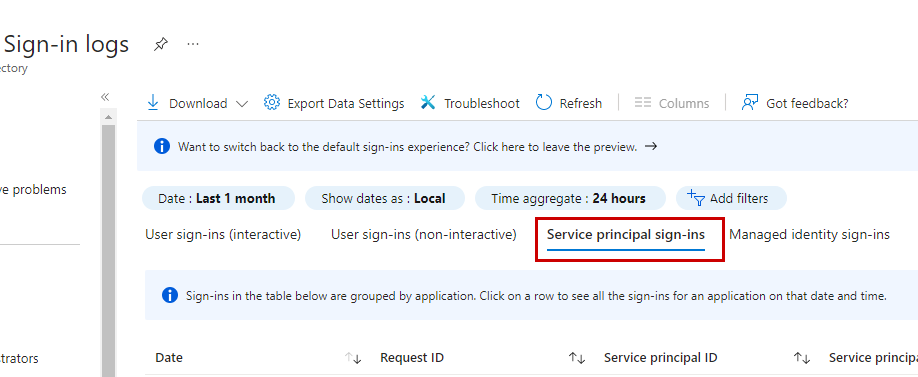
Sign-in logs can be viewed in Azure AD by selecting Service Principal Sign-in Logs. This is where we can see if a service principal sign-in attempt was blocked by conditional access.
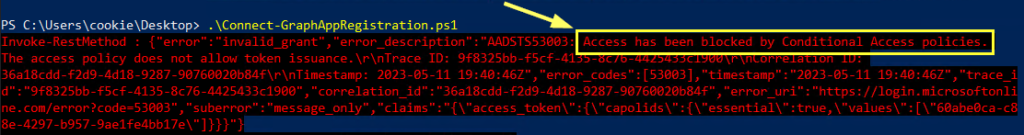
Lastly, let’s test this with PowerShell. I’ll try connecting to graph with my app registration secret key from behind a VPN, so I appear outside the United States. We can see the response that access has been blocked by Conditional Access: