Last year, I wrote a post on deploying the SentinelOne agent for Windows using Intune (Deploy SentinelOne with Intune – SMBtotheCloud). Since then, several people have contacted me asking if I could write a post on how to do this for macOS. So, a few months ago, I picked up a used MacBook to start getting more familiar with macOS and managing Macs with Intune. After learning some of the basics, I decided to make this post and answer the request for a SentinelOne macOS deployment guide with Intune. Plus, the SentinelOne documentation does not contain instructions for macOS deployment with Intune.
Differences between deploying S1 for Windows and macOS
SentinelOne for macOS comes as a pkg. Most pkg files can be uploaded as line of business apps in Intune and be easily deployed to endpoints, similar to how MSI files are so simple to deploy as Win32 or LOB apps on Windows. The big difference here is we don’t have command line arguments in macOS line of business apps like we do for Windows Win32 apps. So, for the Windows deployment, you upload your msi/exe win32 app and then specify your SentinelOne site token as a command line argument. When deploying SentinelOne for macOS, a file containing the site token with the name com.sentinelone.registration-token must exist in the same directory as the pkg installer. The installer automatically looks for that file and uses the site token in that file to register with your SentinelOne tenant. If you’re reading this and don’t know what the site token is, it’s a unique string that identifies your SentinelOne tenant or organization.
Being a macOS newb, I’m still learning tips and tricks for deploying applications, but after a few hours of reading, testing, and trial/error, I decided the best way to do this is through a platform script. This is mostly because we can create the necessary site token file when installing with a shell script. The script will first check to see if SentinelOne is already installed. If it’s installed, end the script. If it’s not installed, create the site token file, download the PKG from blob storage (or another source), and install the application. In addition to installing the application, there are also several profiles that we need to push to our endpoints. Without the profiles, users will end up seeing notifications like the screenshot below where they need to consent to allow the application access to certain resources.
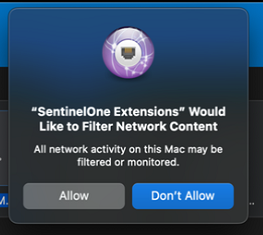
Deploying the Necessary Profiles
As we mentioned at the end of the previous section, some necessary profiles must be pushed to the devices so SentinelOne can properly protect them. Although the SentinelOne KB does not have any documentation on using Intune, they do have documentation on using jamf. We can use the same configuration files and deploy them with Intune. There are four profiles we need to deploy:
- Network Monitoring
- Privacy Control
- Notifications
- Network Filtering
These are available as .mobileconfig files here, or you can get them from SentinelOne’s KB if you have access to their dashboard. For each of these files, we need to create a custom device configuration policy in Intune. From Intune, navigate to devices > macos > configuration. Click Add
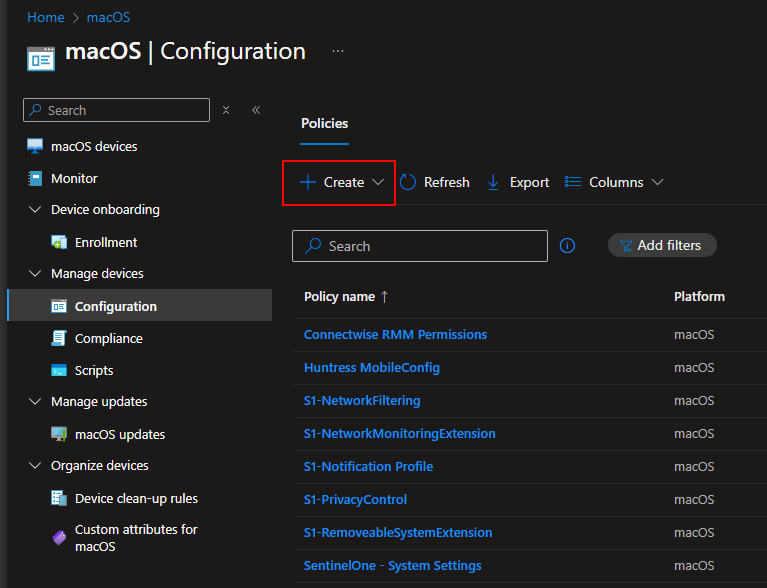
Then select Templates > Custom:
Provide a name for the Intune policy and continue to the configuration settings. Name the profile (this is how it will appear in the macos settings). Select Device Channel as the deployment channel, and then browse to the mobileconfig file.
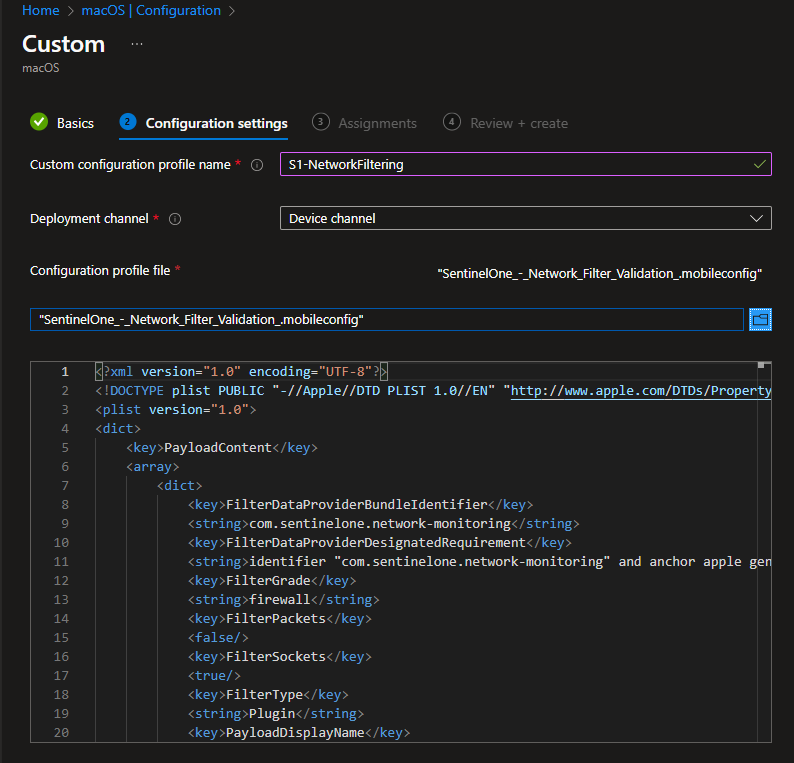
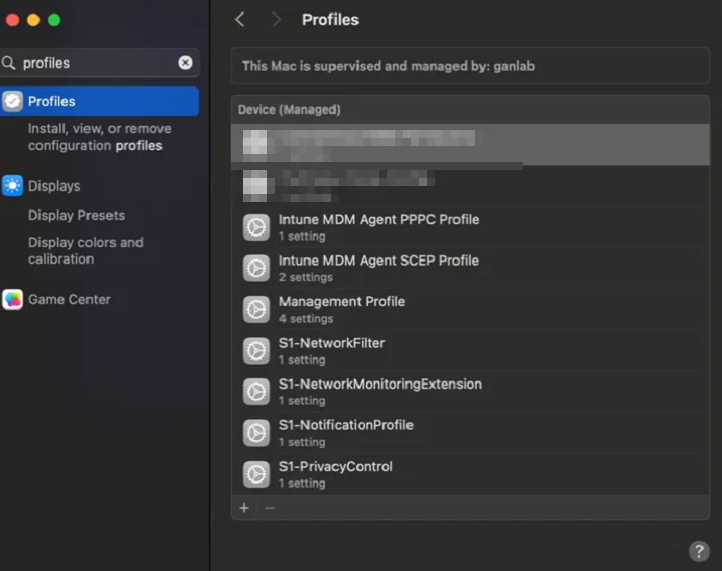
Assign to your target groups, and then repeat these steps for the other three profiles. When these are all deployed, you can find them on the local device under settings > profiles:
The Installation Script
I did not have much bash scripting experience before this, but the concepts of this script are the same as some PowerShell scripts I’ve used for Windows. So, it was pretty easy to pick up the basics. Something nice about Intune macOS shell scripts is that you can run them on a schedule, similar to Windows remediations (you just have a single script instead of separate detection/remediation scripts). So, we can run this script daily or hourly if we want to. The script is below and also available on GitHub here. You’ll need to adjust a few variables found at the top for your siteToken, the URL your pkg download, and the name of the pkg file. The rest of the script does the following:
- Check to see if SentinelOne is already installed. If so, the script stops.
- If SentinelOne is not detected, it downloads the installer file into the /tmp directory
- Creates the com.sentinelone.registration-token file in the /tmp directory
- Installs the SentinelOne Agent and then cleans up the token file
#!/bin/sh
siteToken="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
installerurl="https://yourstorageaccount.blob.core.windows.net/test/Sentinel-Release-24-2-2-7632_macos_v24_2_2_7632.pkg"
installer="Sentinel-Release-24-2-2-7632_macos_v24_2_2_7632.pkg"
dir="/tmp/"
tokenfile="com.sentinelone.registration-token"
if [ -d /Applications/SentinelOne/ ];
then
echo "SentinelOne is already Installed"
exit 0
else
#Download installer into tmp directory
curl -L -o $dir$installer $installerurl
#Create Site Token File
echo $siteToken > $dir$tokenfile
#Install Agent
/usr/sbin/installer -pkg $dir$installer -target /
#Cleanup token file
rm -f $dir$tokenfile
fiAfter you download or create the script file and edit your variables, sign into Intune and Navigate to devices > macos > scripts. Click Add:
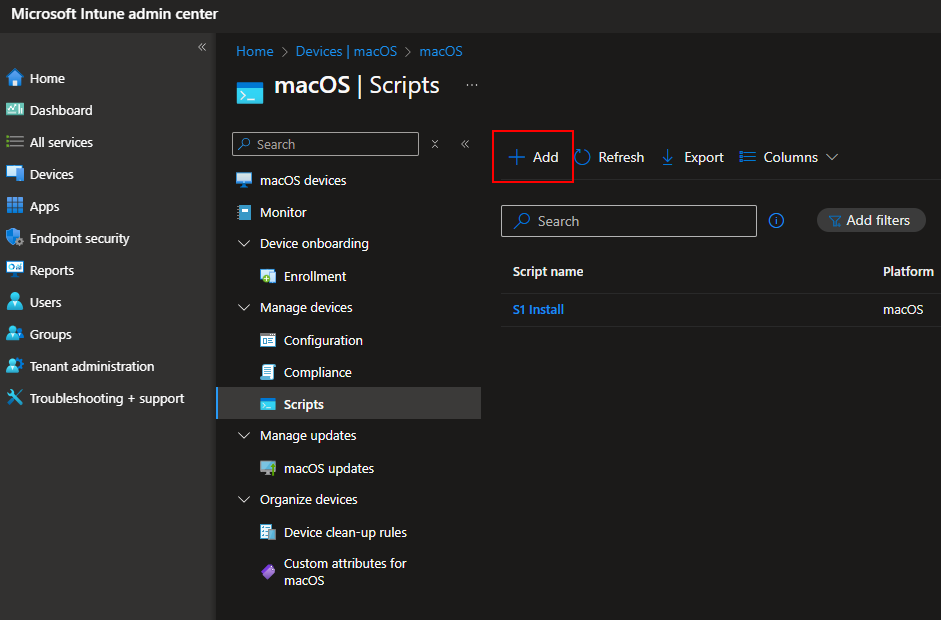
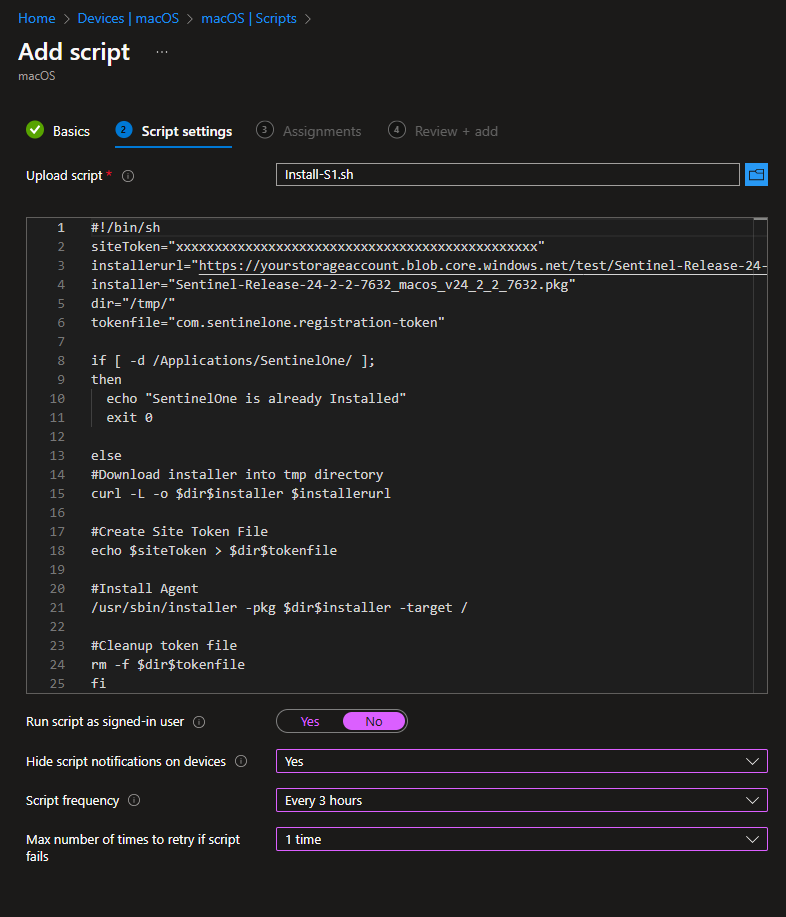
Provide a name, and under script settings, browse to the script file to upload the contents. Select No to run the script as signed-in user. Modify the notifications and script frequency to your liking.
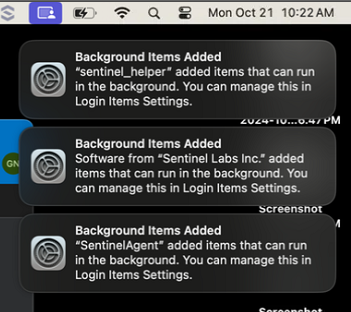
Assign to your groups, and wait for them to check in and get the installer. When the app gets installed on the user devices, they’ll see some notifications about background items:
The devices will show the SentinelOne icon in the status bar, and if it’s opened, it should show online in the top right corner. This means that the site token was applied and the device is reporting to the SentinelOne dashboard:
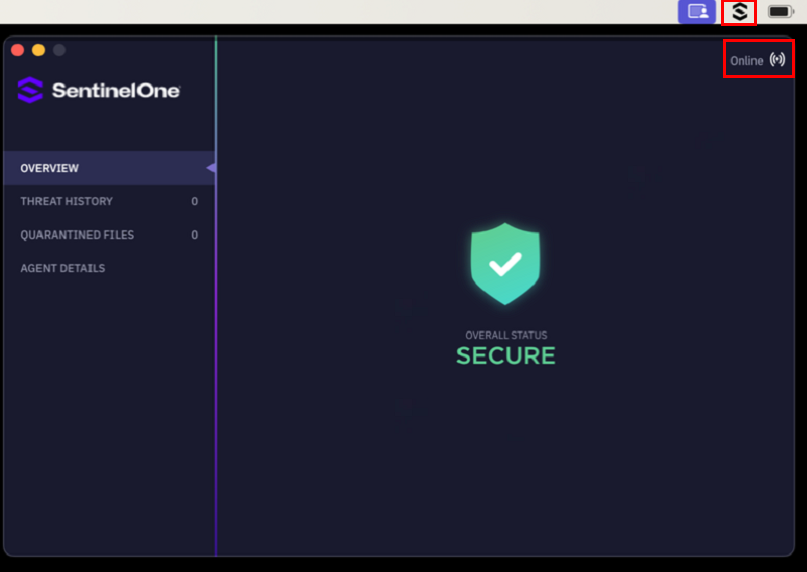
After devices start reporting that the script was successfully executed, you will see results in the device status that the install was successful:
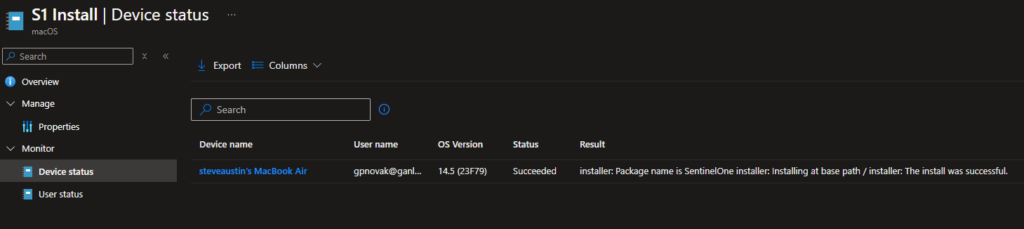
That’s all. For those of you new to SentinelOne who may be wondering how to uninstall the app, the removal is done through the SentinelOne portal. Just remember to unassign the script if you need to remove it from your endpoints.
