Resolve HAADJ Intune auto-enrollment errors for devices previously enrolled in MAM
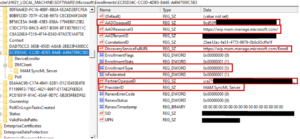
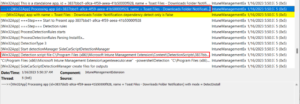
There never seems to be a shortage of issues when dealing with Hybrid Azure AD Joined + Intune Enrolling endpoints. Especially when you inherit a setup and have no history of what was implemented in the past. I encountered a new issue the other day and figured I’d made a quick post. In this situation, […]
Resolve HAADJ Intune auto-enrollment errors for devices previously enrolled in MAM Read More »