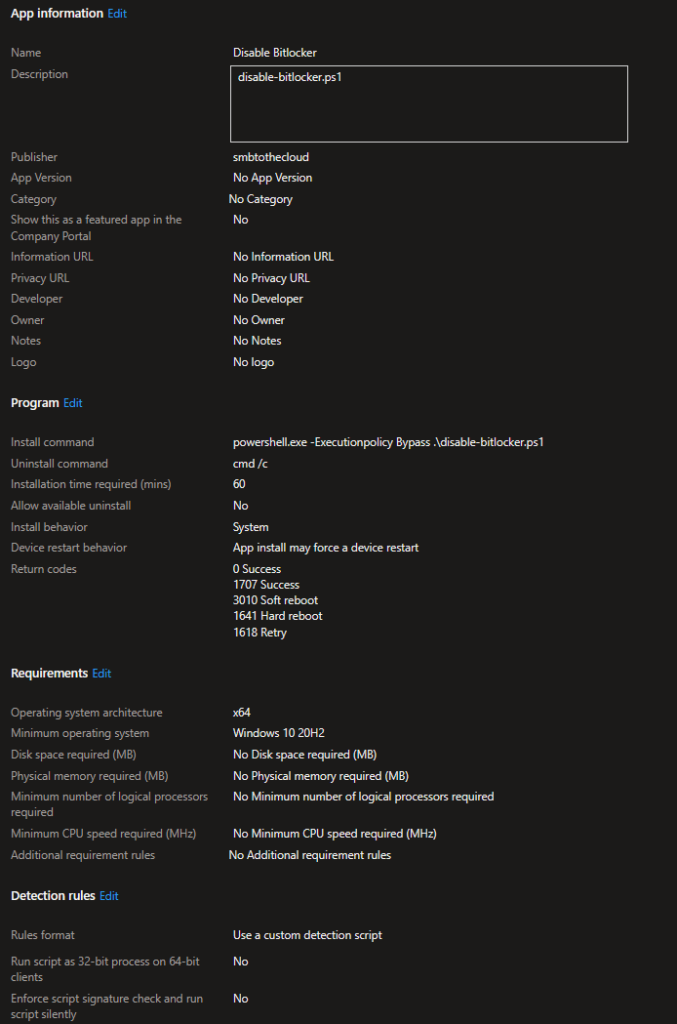
Before I get into this, no, I do not suggest disabling BitLocker or running with decrypted drives in production. BitLocker is good and should be used. However, sometimes clients have requests that we must fulfill. Perhaps they are moving to a third-party encryption solution, or they want to re-encrypt their devices using a stronger encryption method. Whatever the case may be, this blog walks through using a script and Win32 app to disable BitLocker on your devices.
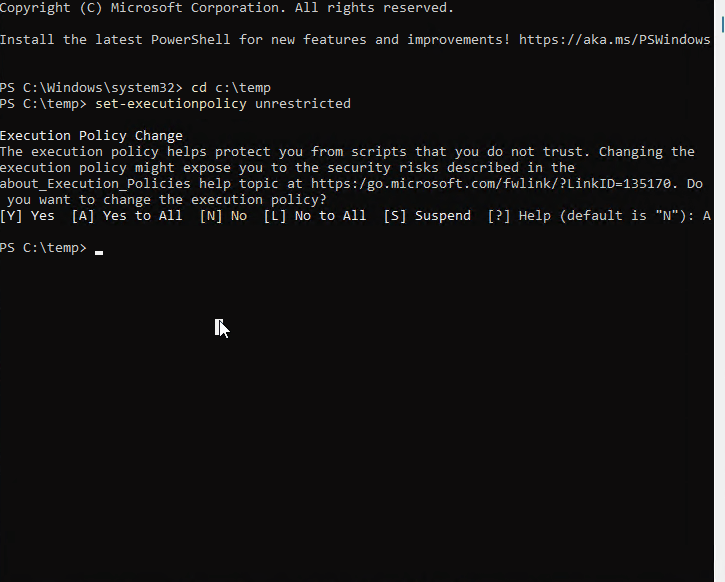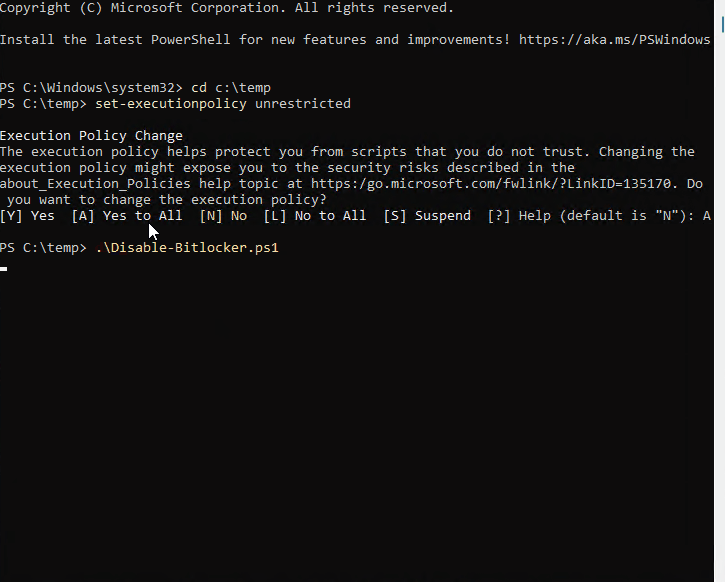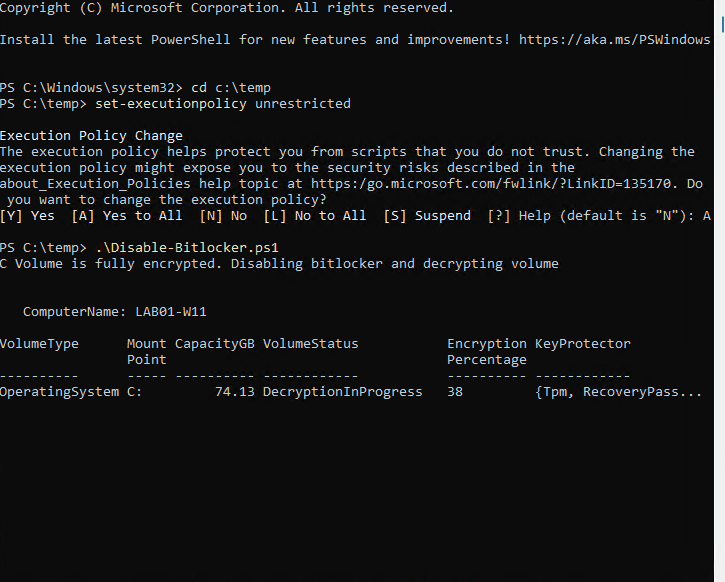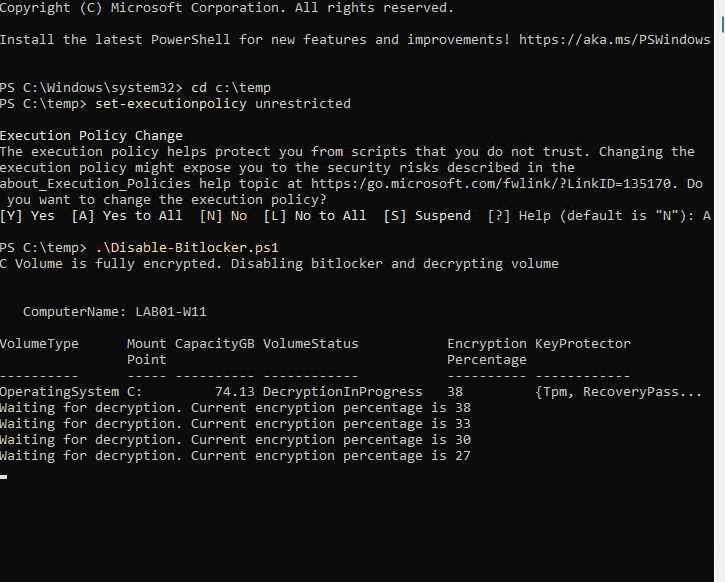
The script is fairly simple and is available on GitHub. For this specific client, we only had system drives to deal with. If you also have data disks, you’ll need make some edits to add the drive status for additional disks. First, the script checks the status of drive encryption. If the status shows that the disk is fully encrypted, then BitLocker is disabled. The Script continues to run and loops every 15 seconds to check the decryption status. We need to do this, so the detection script doesn’t run before decryption is completed. If you happen to run this manually, you’ll also see the percentage as output. If you’re wondering what happens if the system is rebooted while decryption is in progress, it will continue where it left off after the reboot.
$DriveStatus = Get-BitlockerVolume -MountPoint C:
If ($DriveStatus.VolumeStatus -eq "FullyEncrypted") {
Write-Host "C Volume is fully encrypted. Disabling bitlocker and decrypting volume"
Try {
Disable-Bitlocker -MountPoint "C:"
}
Catch {
Write-Host -ForegroundColor Red $_
Write-Host "There was an issue disabling bitlocker"
}
}
$Loop = $true
while($Loop){
$DecryptStatus = Get-BitlockerVolume -MountPoint C: | Select -expandproperty VolumeStatus
$DecryptPercentage = Get-BitlockerVolume -MountPoint C: | Select -expandproperty EncryptionPercentage
if($DecryptStatus -eq "FullyDecrypted") {
Write-Host -ForegroundColor Green "Volume has been fully decrypted"
$Loop = $false
}
Else {
Write-Host "Waiting for decryption. Current encryption percentage is $DecryptPercentage"
Start-Sleep -Seconds 15
}
}Here’s an example of manually executing the script so you can see what it’s doing in the background:
For the detection script, we are simply checking to see if the C volume is encrypted or not:
$DriveStatus = Get-BitlockerVolume -MountPoint C:
If ($DriveStatus.VolumeStatus -eq "FullyEncrypted") {
Write-Output "C Volume is fully encrypted"
exit 1
}
Else {
Write-Output "Detected. Volume is not encrypted"
Exit 0
}The Win32 app should be built just like any other, with the decryption script as the install file. Then, deploy to your desired groups.

Just what I was looking for, thanks for posting.