Several weeks ago, I wrote a script and blog to bulk export Intune policies. That blog can be found here. What started as trying to export/import settings catalog policies in bulk evolved into more, and I added to the script to do more than just settings catalog policies. This is useful for people who often inherit messy tenants or do a lot of new tenant provisioning. When it comes to new tenant provisioning, the import script is a big time saver. If you’re a consultant or engineer, you probably have dozens of policies you configure in all your new tenants. Configuring all these policies manually is time-consuming and subject to human error. Bulk importing all your standard policies will save you time, reduce human error, and make a new client onboarding experience much more efficient.
I hoped to finish the import script sooner, but I kept encountering issues with certain policy types. Exporting the policies as JSON was the easy part. Importing them, however, proved more difficult for some policy types. For example, some policies have dependencies that need to exist before the import, like conditional access or custom compliance policies. For instance, custom compliance policies that rely on a custom compliance script reference the custom script by its ID, which changes when imported into a new tenant. The same is true for conditional access policies with named locations. I am continuing to work on this script to do more, but at the time of writing, this is what can be bulk-imported:
- Settings Catalog Policies (this includes the endpoint security policies)
- App Protection Policies
- OMA URI and Custom Device Configuration Policies
- Remediations
- Tenant Filters
- Platform Scripts
- Compliance Policies & compliance scripts
- Named Locations
This covers almost all the standard configurations I use for most of my new tenants, but I would like to add conditional access policies in the future.
The script can be found on my Github. The Import script is built to work with the export script found here, but you can edit accordingly if you’d like. The export script will export JSON files to respective folders in c:\temp, like the image below.
This can be changed, but the import script will look in c:\temp for all the policy files. Other than that, the script does the rest. It does not assign the policies but imports them into your destination tenant. Depending on the amount of policies you’re importing, it may take a minute or two.
Regarding the compliance policies, a reference file is generated during the export, which maps any custom compliance policies to the ID of the custom compliance script. This is used during the import and will update the compliance policy to use the new script ID after it’s imported. I kept running into issues where there was a delay in the compliance script imports, and the IDs would not be available for a few seconds to a few minutes. So, the script will pause while it checks to ensure all the custom compliance scripts have been imported before continuing. It’s also important to note that if the reference file is deleted, then any custom compliance scripts will fail to import.
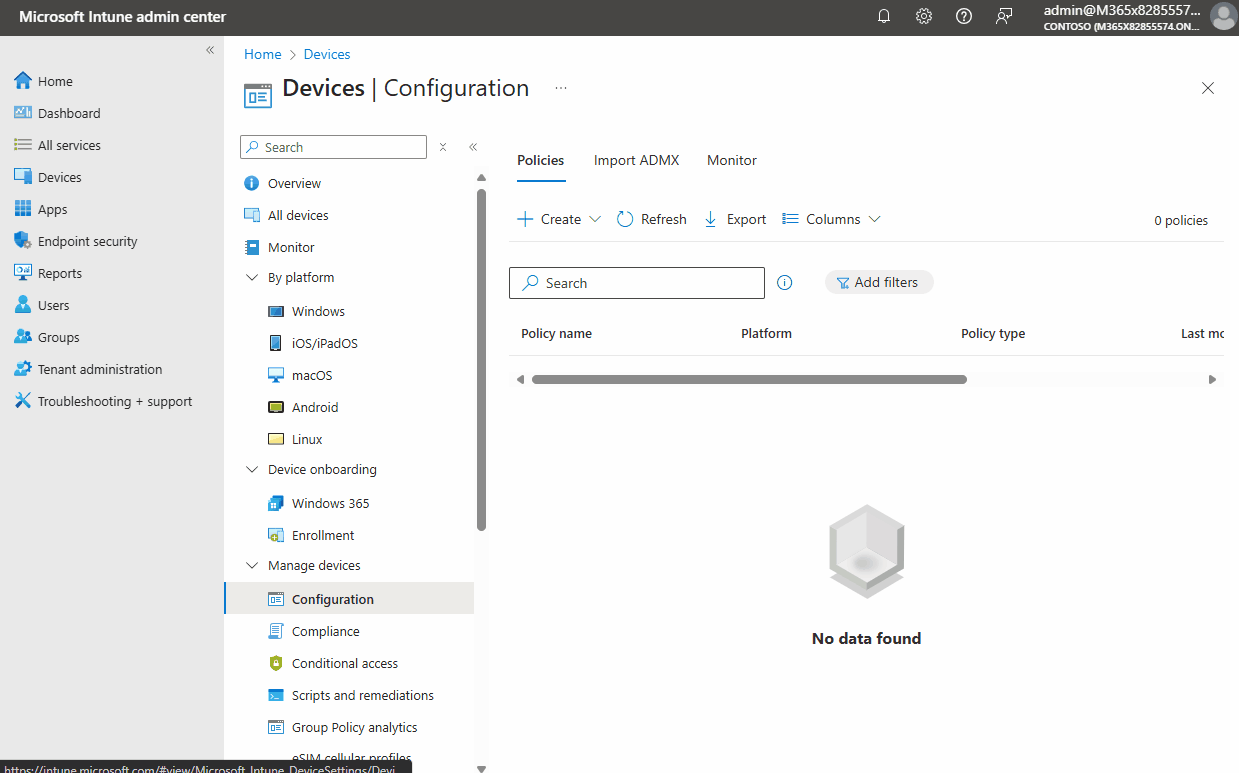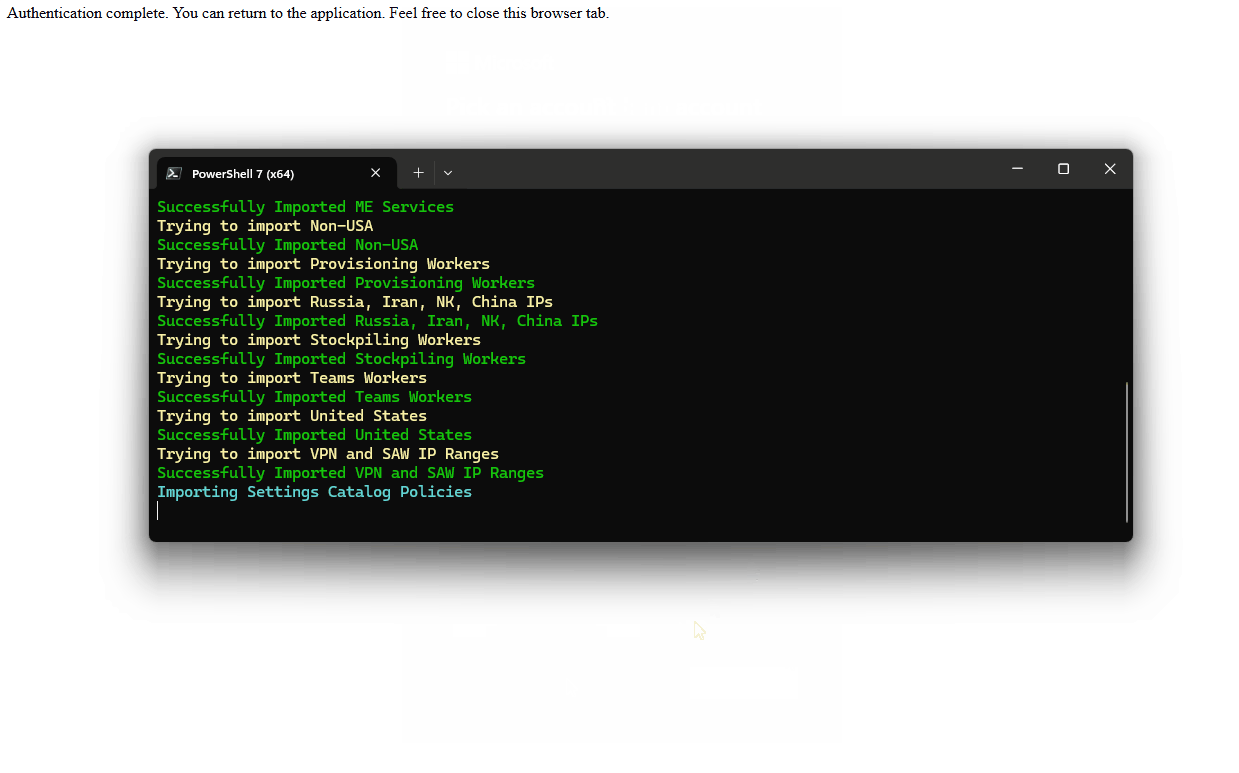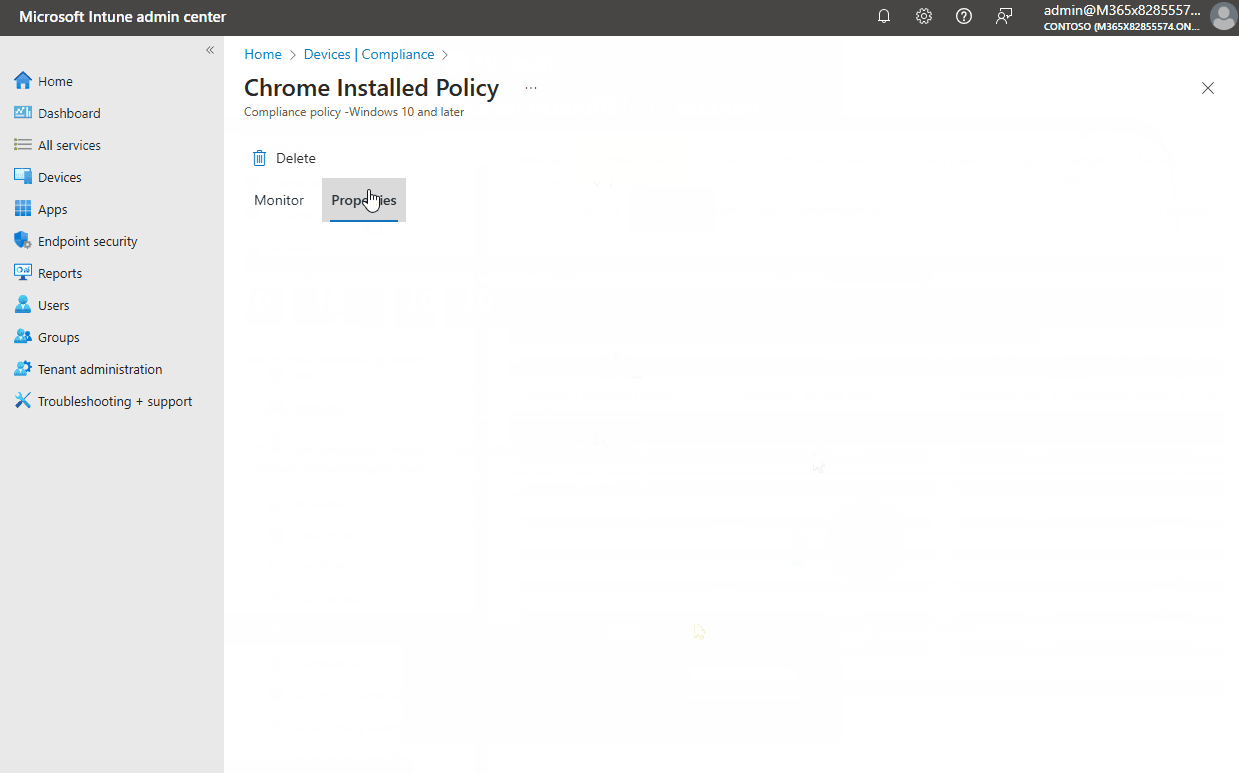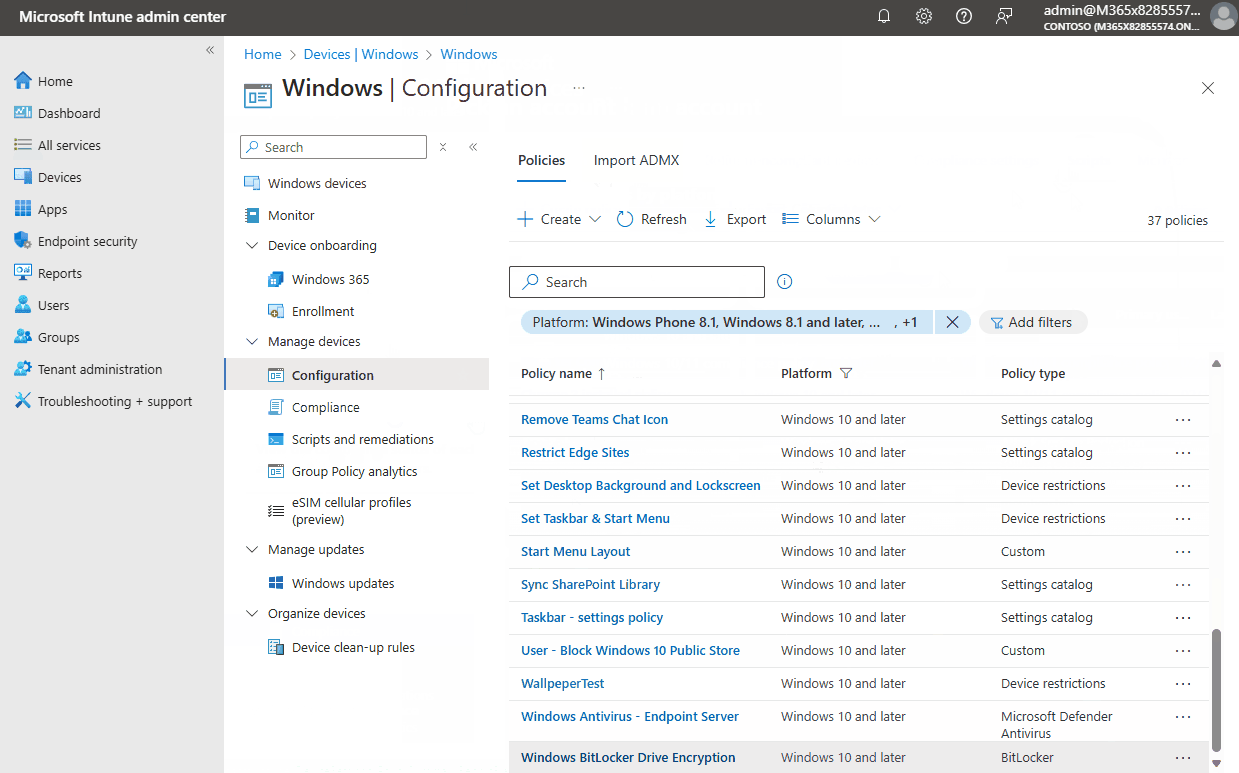
Here’s an example of the script running to import policies into a new demo tenant: