A few months ago I had to deploy the SonicWall Global VPN client and configuration using Intune. The blog post on that is here – Deploy the SonicWall Global VPN client + Configuration Settings with Intune – SMBtotheCloud. Recently, some of these devices started experiencing general slowness on websites and apps that required internet access. After a bit of research, this was only occurring while the clients were connected to the VPN. That led to this SonicWall KB – GVC : Degraded Internet throughput from local ISP even though connected in Split tunnel | SonicWall. These devices were fully updated and running Windows 11, but testing this fix on a device resolved the issue. So, since all the devices are enrolled in Intune, we can push this fix out with a remediation or Win32 app. In this case, I’ll use a Win32 since the client is not licensed for Remediations.
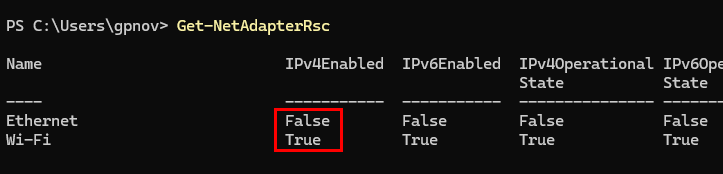
In general, you don’t want to disable RSC on your network adapters. Network Adapter RSC is a hardware optimization feature that minimizes the number of TCP/IP packets the CPU needs to handle by combining smaller packets into larger ones directly on the network adapter. This enhances CPU efficiency, increases throughput, and reduces latency, making it especially useful in high-traffic or virtualized environments. For an individual computer doing typical business tasks, this shouldn’t cause any performance issues. This script only disables RSC on the Wi-Fi adapter since the affected devices are all laptops that only use Wi-Fi. This was also suggested as a fix from SonicWall. You can manually check the RSC configuration on your network adapters in PowerShell with Get-NetAdapterRsc:
There are three options to implement this – Platform script, Remediation, and Win32 app. Links are below for the Win32 App and the Remediation scripts.
- Win32 App – MS-Cloud-Scripts/intune/SonicWallGVC/Win32-DisableRSC at main · gnon17/MS-Cloud-Scripts (github.com)
- Remediation – MS-Cloud-Scripts/intune/SonicWallGVC/Remediation-DisableRSC at main · gnon17/MS-Cloud-Scripts (github.com)
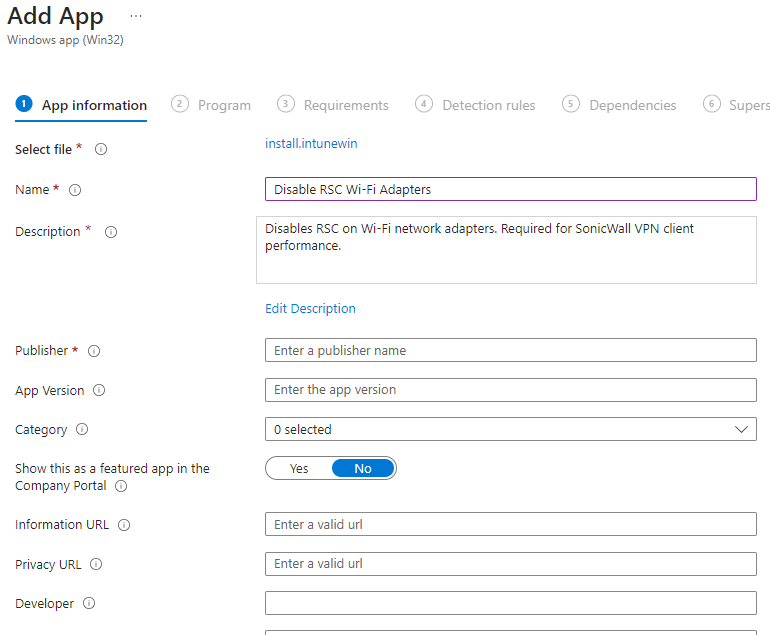
Download the .intunewin file from the link above, or modify the script as needed and repackage as a .intunewin file. Create the new Win32 app in Intune.
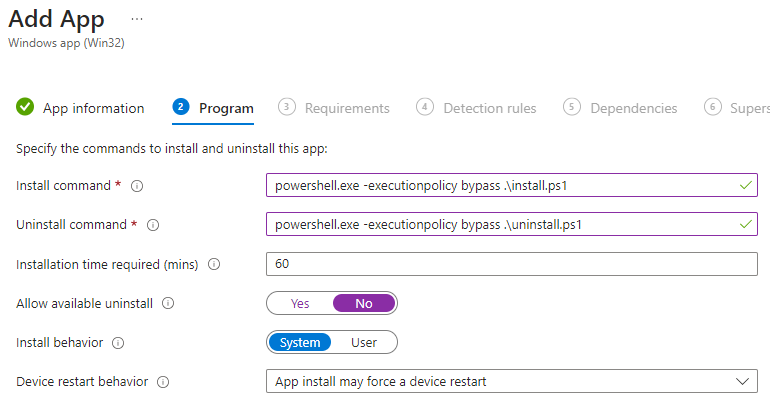
Our install and uninstall commands are standard per the scripts. The uninstall script reverses the action and re-enabled RSC on the Wi-Fi adapters:
- powershell.exe -executionpolicy bypass .\install.ps1
- powershell.exe -executionpolicy bypass .\uninstall.ps1
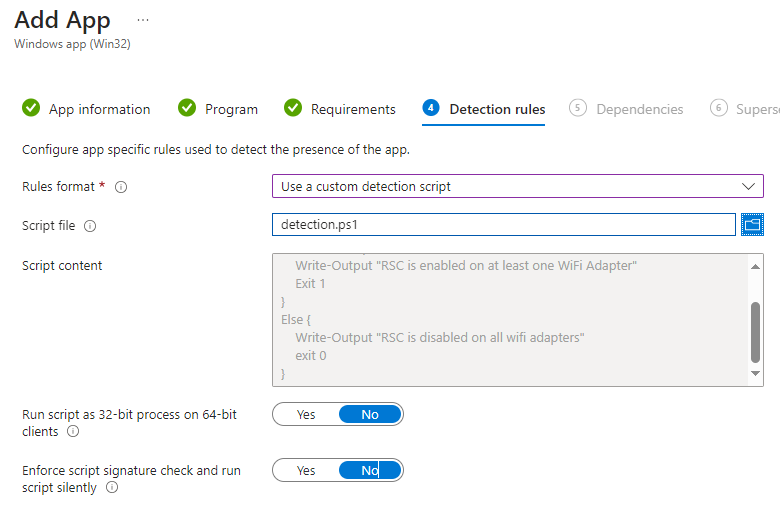
The detection script from the GitHub link above will look for any connected WiFi adapter and the RSC configuration:
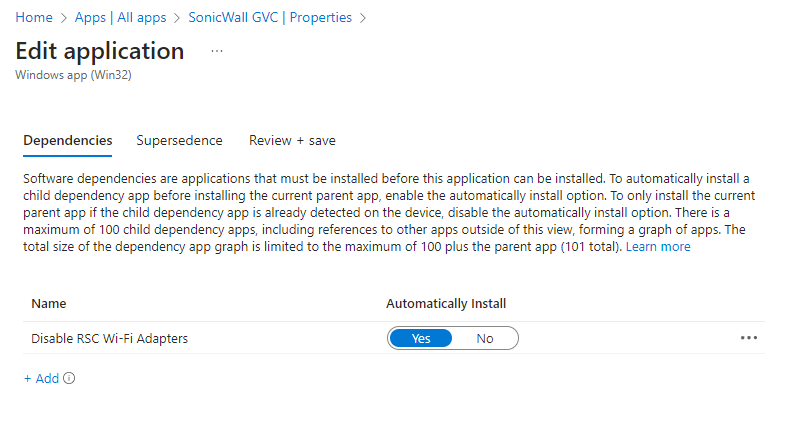
Assing to your devices to finish up. If you want to – you can make this a dependency for your SonicWall Global VPN client deployment: