This seems to come up every once in a while, as a question on Reddit or on LinkedIn – How can I block browser Internet access or only allow access to certain sites on an Intune managed device? This post will cover how to completely block internet access from web browsers and how to only allow access to certain URLs. Using the methods in this post are only going to be beneficial if you want to block access to all URLs from browsers, or if you have a list of static URLs where you want to allow access. If you’re looking to do URL filtering or dynamically block categories of sites, you should look at the web filtering component of Defender for Endpoint/Business.
Option 1 – Settings Catalog for Chrome/Edge
Assuming you are only using Chrome and/or Edge in your environment, the easiest method is to use a settings catalog profile. Both Chrome and Edge support a configuration setting to “block access to a list of URLs”. In my opinion, unless you have a static set of specific URLs you want to disallow, this should be set to all sites (by using * as the value) so you can whitelist only what you want to allow. The example policy below has these settings highlighted:
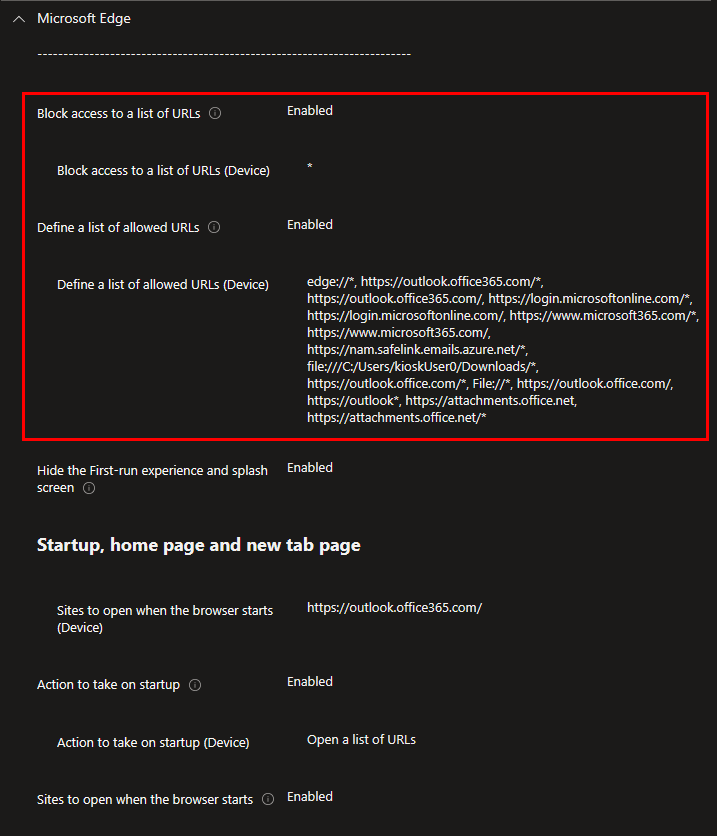
If user tries to access any site not specifically whitelisted, they’ll receive the below message:
In addition to those highlighted settings, the example policy shown above does a few more things if you want to do more than simply whitelist certain sites. For example, I did a Kiosk setup for an organization several months ago where they only wanted to allow access the web version of outlook, but also allow the user to download/view PDF file attachments. By using Edge as the PDF viewer, we whitelisted the download location and additional URLs for safe attachments. Some additional settings to hide the first run experience and to open the browser to web Outlook are also in this policy. This policy uses Edge, but all the equivalent settings are available in Chrome, also.
This example policy can be deployed to your tenant using this script. Simply run it and it will add the policy named “Restrict Edge Sites” to your environment.
If you’re wondering where these settings are applied on the local device, or you want to confirm your policies are being applied, you can visit the registry key HKLM\Software\Policies\Microsoft\Edge. There are a few subkeys with corresponding values we set in the configuration policy.
HKLM\Software\Policies\Microsoft\Edge:
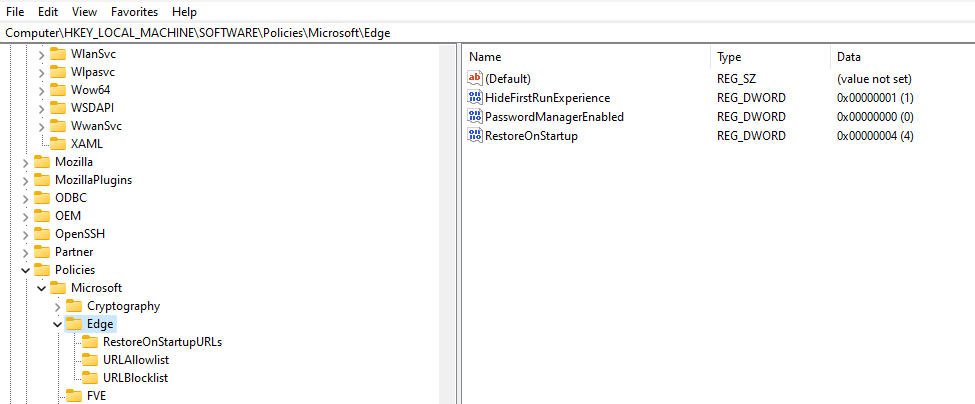
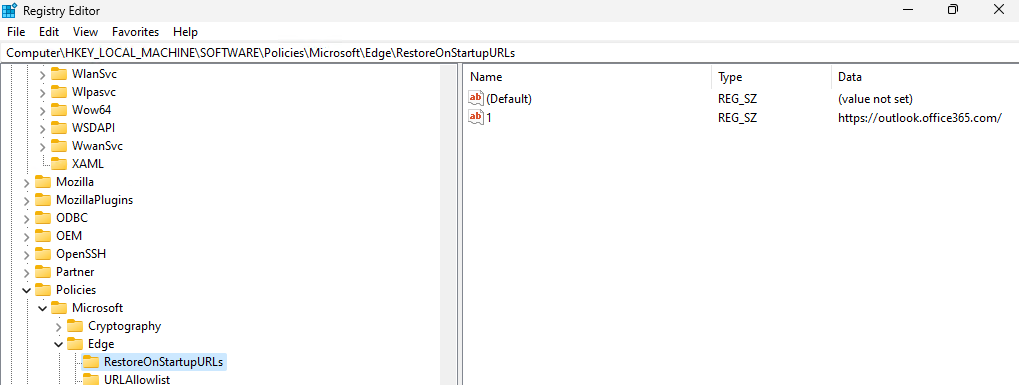
HKLM\Software\Policies\Microsoft\Edge\RestoreOnStartupURLs:
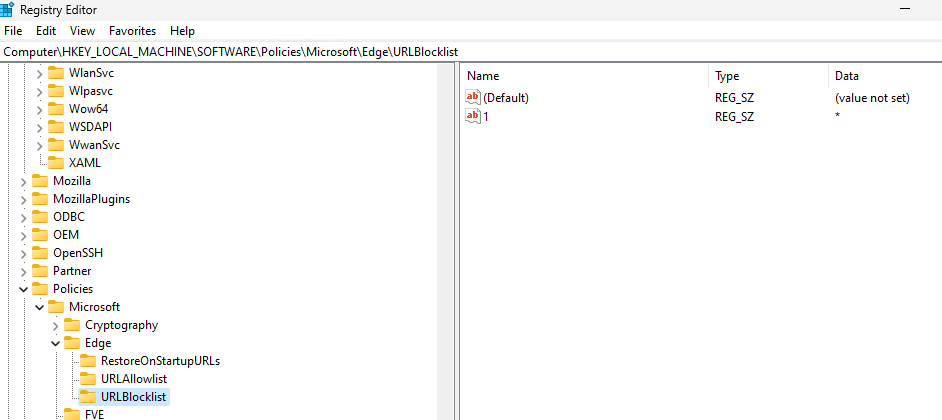
HKLM\Software\Policies\Microsoft\Edge\URLBlocklist:
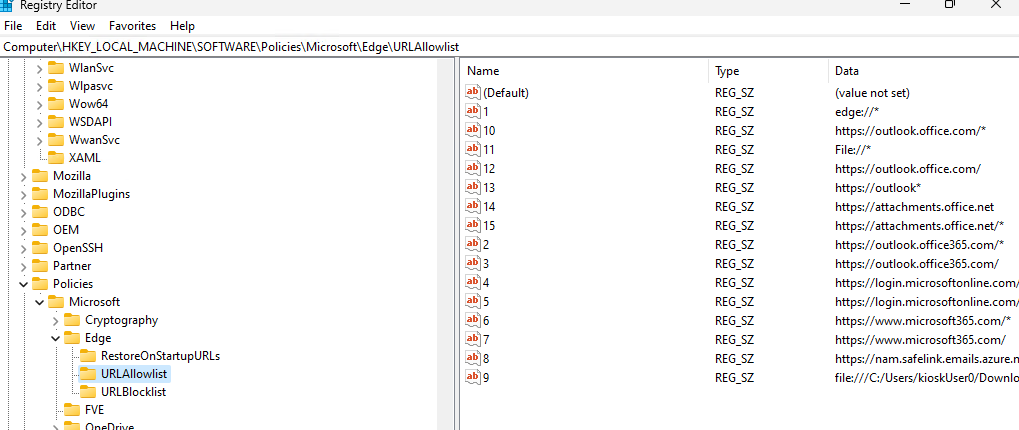
HKLM\Software\Policies\Microsoft\Edge\URLAllowlist:
Option 2 – Use Windows Firewall
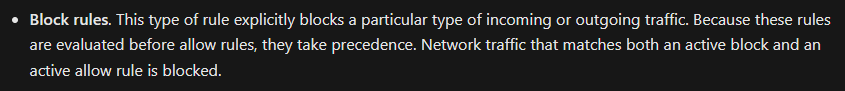
Like we mentioned earlier, if you’re using Chrome/Edge, the settings catalog policy described in Option 1 is going to be a more flexible and easier deployment. However, if you’re using other browsers in your environment or want to block more apps than just browsers, you can use Windows Firewall rules. For this configuration, we simply target the apps we want to block with an outbound rule blocking port 80 and 443. Using Windows Firewall, you can only specify IP addresses, not domain names. Also, using this method won’t allow you to make specific exclusions since block rules take precedence over allow rules:
I tried making exclusions anyway just to see what happens. You’ll end up having your allowed rules “optimized out”, meaning they are irrelevant and won’t change what is blocked/allowed.
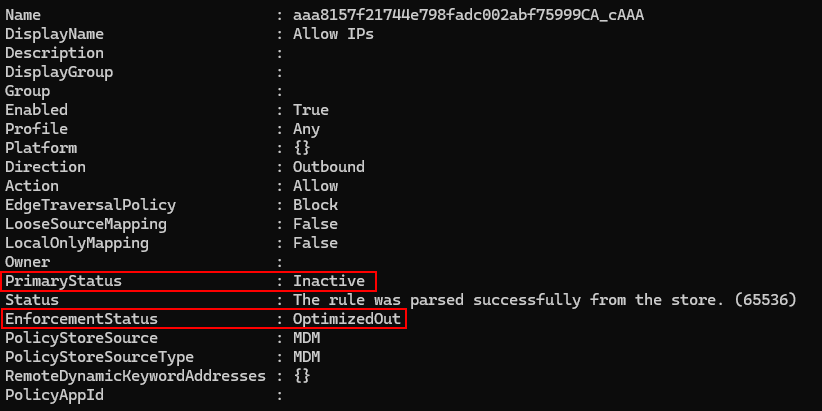

So, if you’re using this method, you’ll likely be blocking all Internet traffic from your targeted apps. So, you don’t get as much flexibility with the ability to make exclusions by domain name. Nevertheless, this will still block port 80/443 internet traffic for browsers or other apps, if needed. One other thing I should mention is I did not explore any ADMX files for Firefox, Brave, etc. They may have equivalent settings we discussed in option 1, but you’ll need to check that if it applies to you and import the ADMX file.
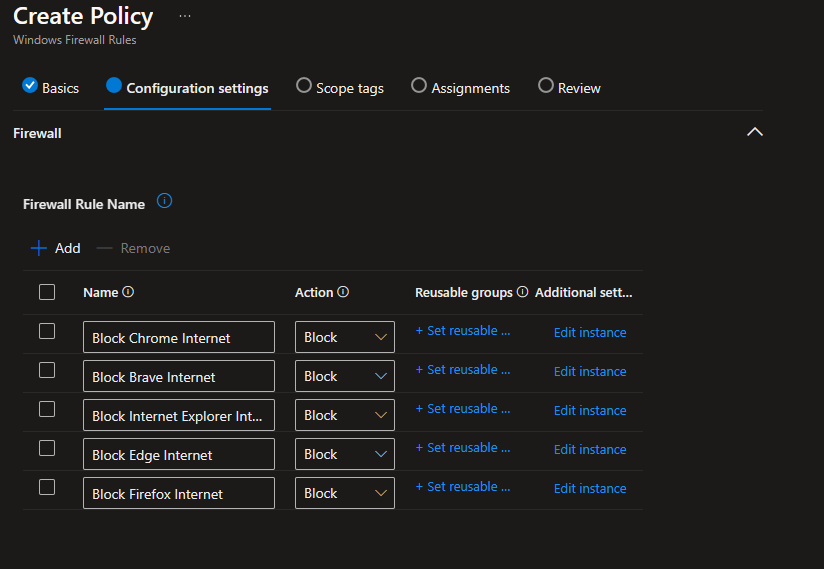
Here’s an example firewall policy that blocks common browsers from accessing the internet. This policy can be added to your tenant by running this script if you’d like to use it as a template.
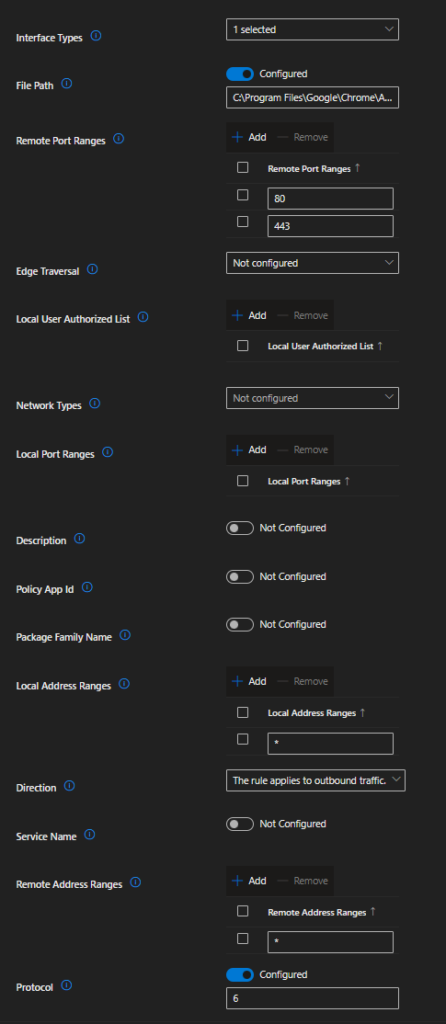
And one of the rules, which specifies the path to the browser and protocol (TCP):
After the policy is applied, you can confirm the rules have been added by navigating to HKLM\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\MDM\FirewallRules:
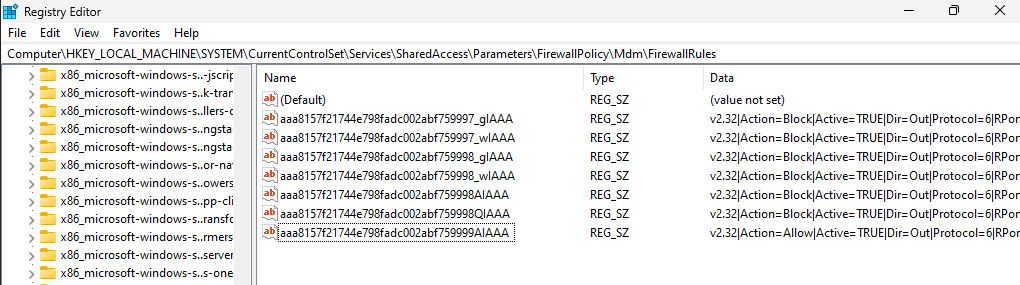
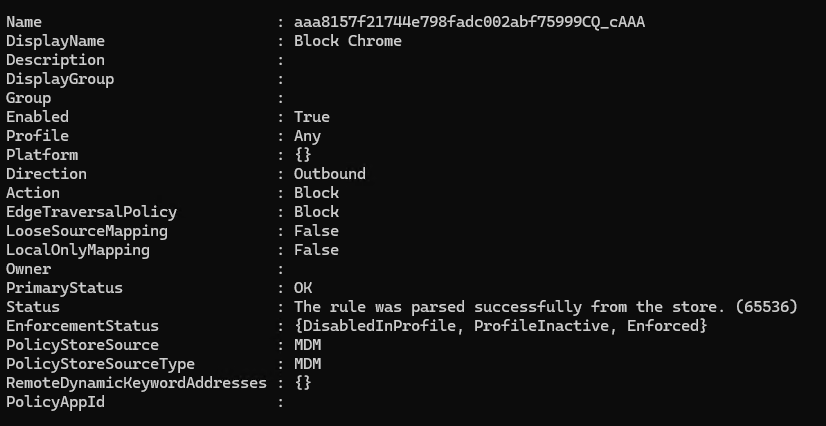
And then you can confirm they are active by using PowerShell command Get-NetFirewallRule -PolicyStore ActiveStore. The additional MDM added rules should be listed at the bottom:
Lastly, if users try browsing to the internet, they’ll receive a message like this: