I do a lot of MAM rollouts. Most of them go off without a hitch and any issues are usually resolved by reinstalling the application. However, I encountered a couple of issues recently and figured I’d share this. I should say that I’ve rolled MAM out to thousands of devices and this is the first time I encountered this issue. So, it’s likely you won’t see this, but if you do, it’s the users who need to fix something on their side. And, it’s embarrassing for them when you tell their manager why MAM wasn’t functioning on their device.
The Situation and Error
This occurred on two iOS devices out of roughly 400+. The two affected users stated that when they got to the step where they were supposed to set a passcode to access the protected app, it was telling them a passcode was required. We did the normal troubleshooting of reinstalling the app and deleting the device registration to get the device re-registered. However, they continued to get the same error. MAM issues can be difficult to troubleshoot because you often don’t have hands on the device, and these are usually personal devices. So, there are variables you can’t control. Plus, when something is working on 99.5% of devices, your policies aren’t to blame. Here is the error they were receiving when trying to access Outlook or Teams:
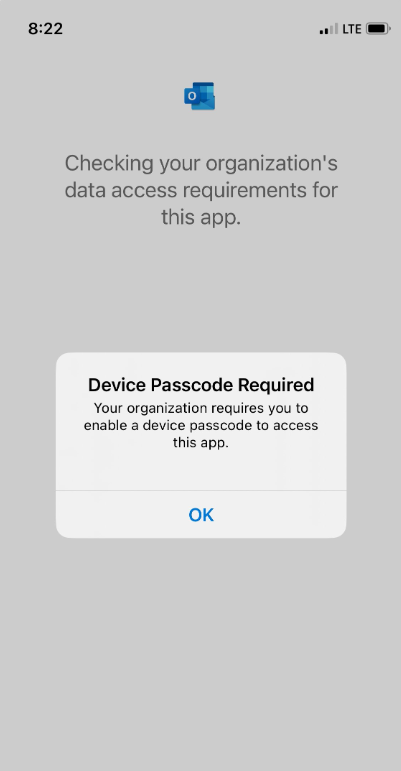
The error states that a passcode is required. When dealing with users remotely and they’re verbalizing that it’s saying a passcode is required, I assumed that this was referring to the access requirements, since I always use PIN access requirements in the app protection policy. After all, access requirements ensure that a user who does not have a passcode set on their device still has a layer of protection to access company data, right? But, if you read the whole error, it states “Device Passcode Required. Your Organization requires you to enable a device passcode to access this app”. So, a DEVICE passcode is required, which is different than the PIN access requirement that simply gets us into our MAM-protected apps.
How could this be working on so many devices but only two of them had this error? Well, after digging through everything I could find, I stumbled on the tooltip for the Encrypt Data setting in the app protection policy:
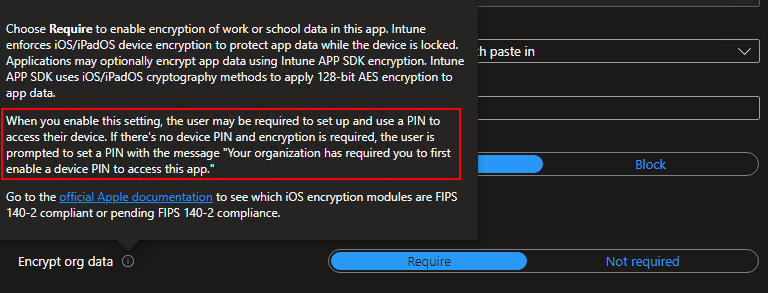
We can see that if Encrypt org data is required, which it always is on my policies, it says “When you enable this setting, the user may be required to set up and use a PIN to access their device. If there’s no device PIN and encryption is required, the user is prompted to set a PIN with the message Your organization has required you to first enable a device PIN to access this app”. This is exactly the error the affected users were receiving. I didn’t think it was possible that in 2024 people would still be out in the wild without any sort of device passcode, but to my surprise, after asking these users if they had a device unlock passcode, they admitted they did not. So, setting a device PIN/Biometric instantly allowed them to access their corporate apps and data. Easy Fix. But why is a device passcode necessary for encryption?
Encryption on iOS devices
On iOS devices, when a passcode gets set, the device automatically generates an encryption key that is associated with the passcode. Essentially, setting a passcode will also encrypt your device data. When the device is locked, the data on the device is encrypted until it is unlocked with the passcode or biometric. This is a good feature. You can validate that encryption is enabled on your device by Navigating to Settings > Face ID and Passcode and scrolling to the bottom. You’ll see “Data Protection Enabled”. Again, as long as you have a passcode set, this should automatically be enabled.
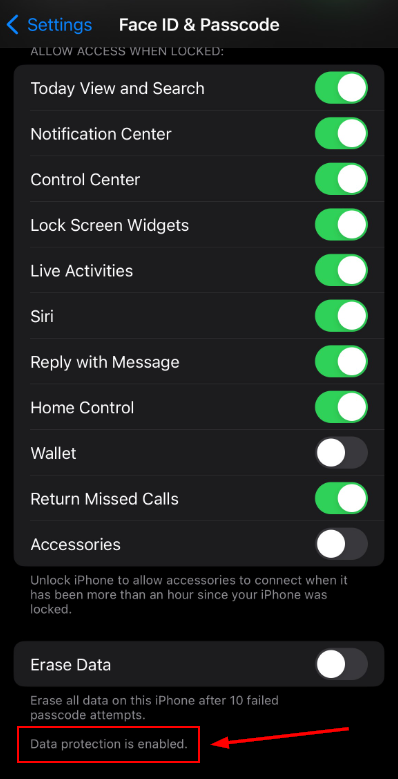
Intune relies on iOS device encryption for the app protection policy requirement. So, if you require encryption on your app protection policies, the only way this data can be encryption is if a device passcode is set. Remember, since these are personally owned devices, we have no way to require they set a PIN, so they’ll simply receive a notification. And in all honesty, if someone went through the trouble of not setting a device PIN, they probably shouldn’t be handling company data on their device.
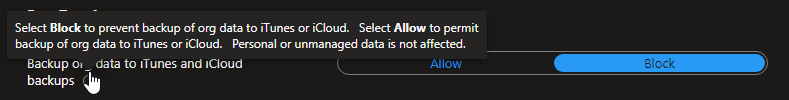
I also suggest blocking backing up company data to iCloud. Although iCloud data is encrypted, Apple maintains the encryption keys and you also don’t want users to have a backup of any corporate data they can restore.