Force Password Change at Next Sign-in for Entra Connect Synchronized Identities
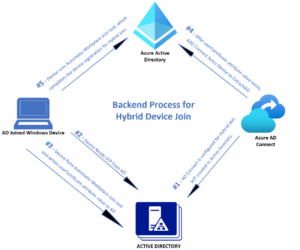
Here’s a quick tip if you’re using Microsoft Entra Connect (Azure AD Connect) to sync your user identities, and you need to enforce a password change for users at the next logon. This can be useful if your user identities are all synced from AD but you have a mixed bag of devices with PCs […]
Force Password Change at Next Sign-in for Entra Connect Synchronized Identities Read More »