Last updated on May 30th, 2024 at 12:58 pm
If you configure an Azure environment with strict networking rules, like no or limited internet access, you may experience issues with Windows Activation on your VMs. This also extends to Win10/11 Pro & Ent for AVD and Windows 365 cloud PCs (if using vnet integration). Some of the screenshots below are what you may see if an Azure Windows OS is unable to activate:

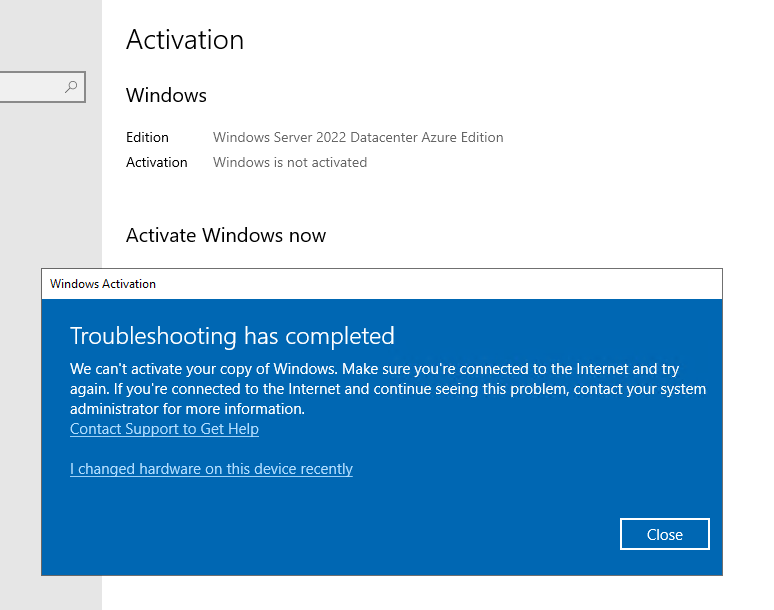
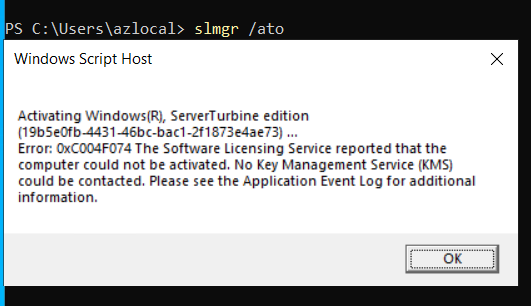
We can see in the final screenshot that it specifically mentions KMS could not be contacted. Azure Windows operating systems rely on an Azure-hosted KMS server for activation. In this specific environment, an Azure firewall was added. If you didn’t already know, Azure firewalls come out of the box with an implicit deny and will only pass the traffic specified in your rules.
Azure VMs need to make outbound connections on port 1688 for KMS. The KMS services operate using the FQDNs and IPs shown below (for Azure global):
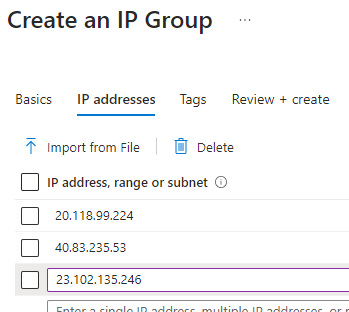
- 20.118.99.224, 40.83.235.53, 23.102.135.246
- azkms.core.windows.net -and- kms.core.windows.net
There’s a tutorial here providing the IPs and FQDNs if you don’t use Azure Global. It also provides instructions on how to do this with a route table, but if you have Azure Firewall and want to funnel all network traffic through it, you’ll need to create some network rules. This is a necessary service, so if you are limiting outbound access, you need to create a rule to allow for Windows KMS activation.
Since I am using a Standard SKU of AZ Firewall without DNS Proxy enabled, I’ll make an Azure IP group and specify the IPs instead of the FQDNs:
Next, create a new Network Rule collection in your AZ firewall policy or add a new network rule to an existing rule collection. This is straightforward. Remember, Azure Firewall blocks all traffic by default. So, if you don’t have a default route for the internet (which we didn’t in this environment), then all outbound traffic is blocked except for what is specifically allowed. When you create the rule, provide a name indicating its purpose. The source will be your VM or subnet containing VMs that needs to access activation services. I suggest creating an IP group for this, also. Our destination port is 1688, which is required for KMS, and our destination type is the IP group we created in the previous step, which contains the required KMS IPs. We don’t need an inbound rule since AZ Firewall is stateful. Your rule should look like this:
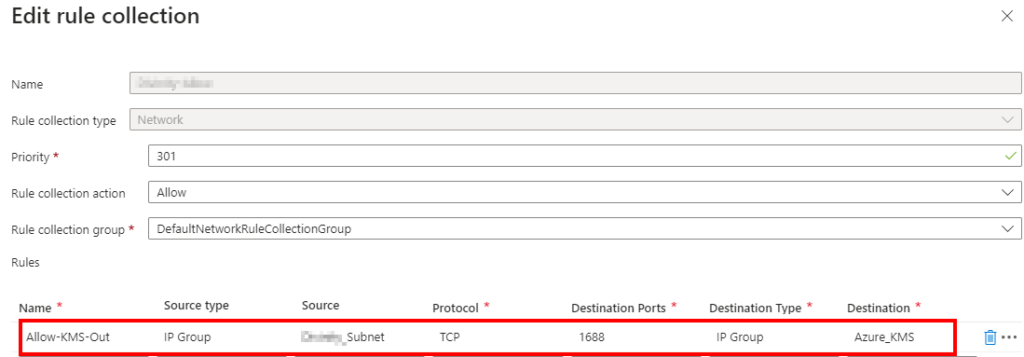
After saving your rule, wait a few minutes and then test connectivity using test-netconnection in PowerShell:
Test-netconnection 20.118.99.224 -port 1688 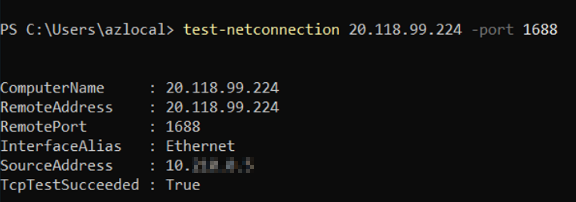
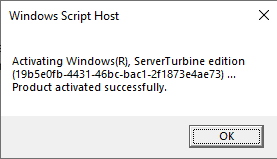
If your test succeeds, we can try activating Windows with slmgr /ato
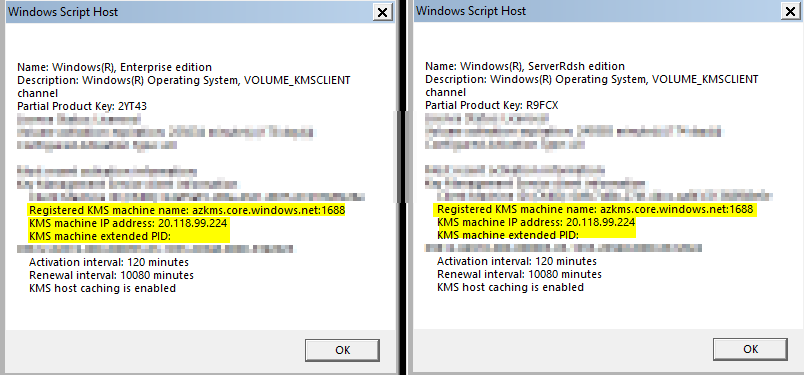
Lastly, if you want to check if an Azure VM (this includes guest OSes for Win10/11 multi-session and Windows Enterprise/Pro). We can issue slmgr /dli and it will show us the activation information. In the screenshot below, we can see a Windows 11 cloud PC on the left and a Win11 multi-session AVD host on the right: