If you didn’t already know, per user MFA can cause issues when connecting to Entra-Joined Azure virtual machines. Specifically, AVD and Windows 365 instances. When this happens, you will get an error when signing in like this:
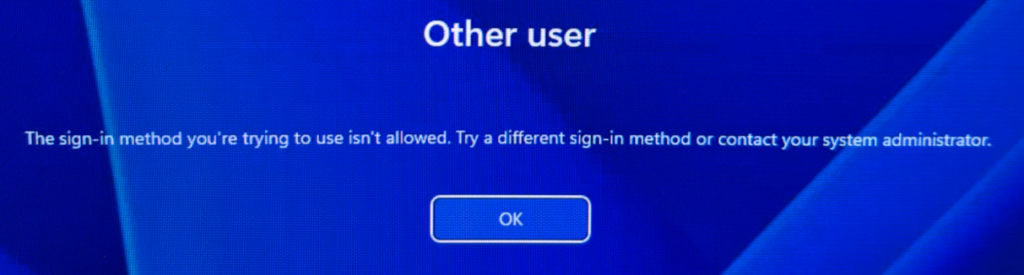
That error is almost always pointing to one of two things:
- Your Conditional Access MFA policy does not have the Azure Windows VM Sign-in app excluded
- Per-User MFA is still enabled or enforced on that user
I had an interesting situation where we were piloting an Entra-Joined AVD pool for an organization. Although most users could sign in without issues, some received the above error. After confirming that the Azure Windows VM Sign-in app was excluded from the Conditional Access MFA policy, I turned to the per-user MFA settings. This organization uses conditional access, so as expected, I did not see any of these affected users with per-user MFA enabled or enforced in the dashboard:
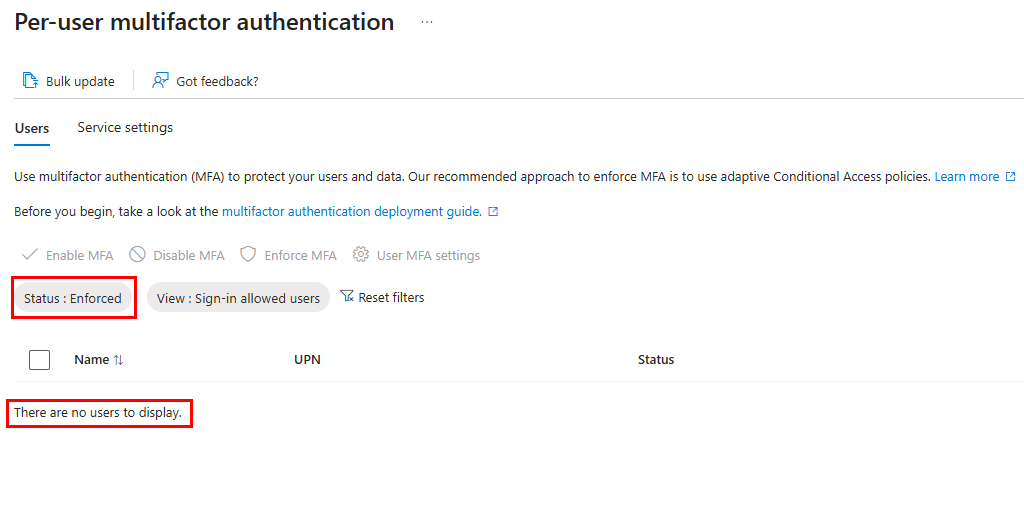
After more troubleshooting, signs still pointed to per-user MFA or the Azure Windows VM Sign-in app. I thought maybe the filtering was broken in the per-user MFA section, so I searched specifically for an affected user and received no results.
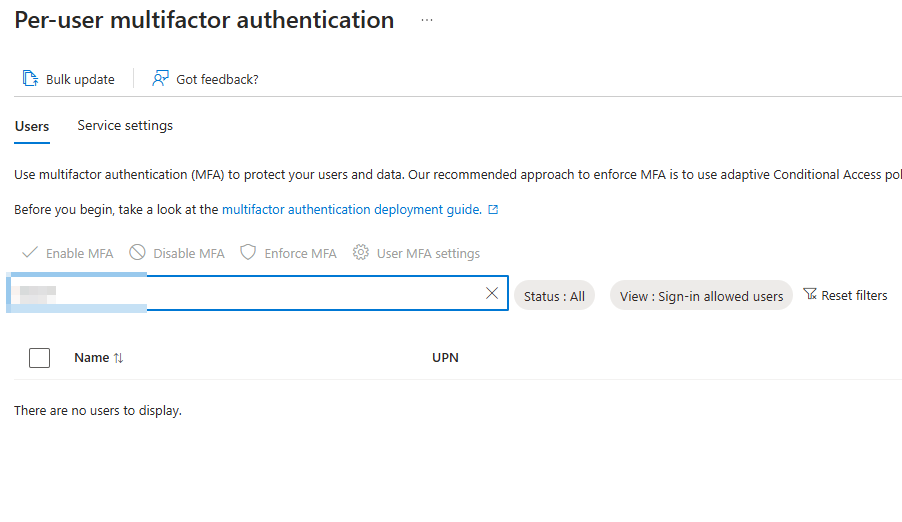
I knew this user existed, so I cleared all filters and browsed through the list of all users to realize that the user was not even listed in the per-user MFA dashboard. This seemed strange because I had no confirmation that per-user MFA was disabled for this user. I checked a few other users and found that the per-user MFA list of users was incomplete.
I turned to the MS Graph to see if I could find this information. Using the graph explorer is great for spot-checking a few users. The graph resource you can use to check a user’s per-user MFA status is – https://graph.microsoft.com/beta/users/<userID>/authentication/requirements
Lo and behold, searching for one of these affected users showed their per-user MFA status as enforced:
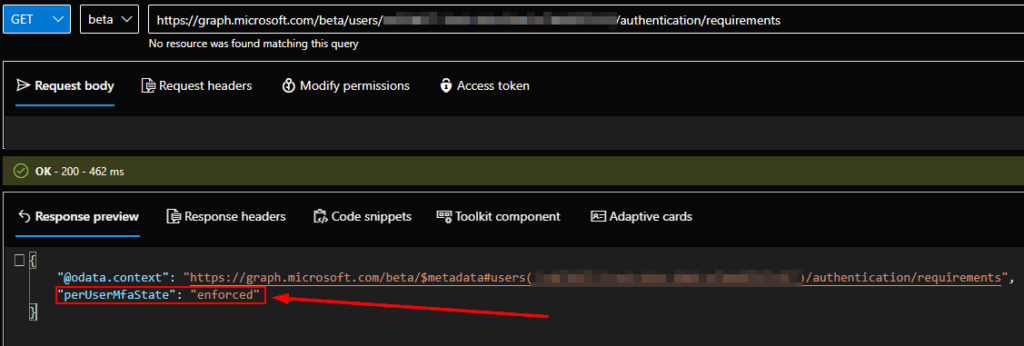
This is the culprit, but since this user doesn’t appear in the GUI, how can we disable their per-user MFA state? Before we get into that, if your organization uses Conditional Access, you should disable per-user MFA for all users and manage MFA with conditional access. A couple of years ago I made a post that walks you through that process – Move from per-user MFA to Conditional Access MFA in Azure AD – SMBtotheCloud.
However, if you want to do this using the graph explorer to test with one user, we can do it like this:
Change the graph request method to PATCH and then add the below syntax as the request body:
{
"perUserMfaState": "disabled"
}Then, click Run Query.
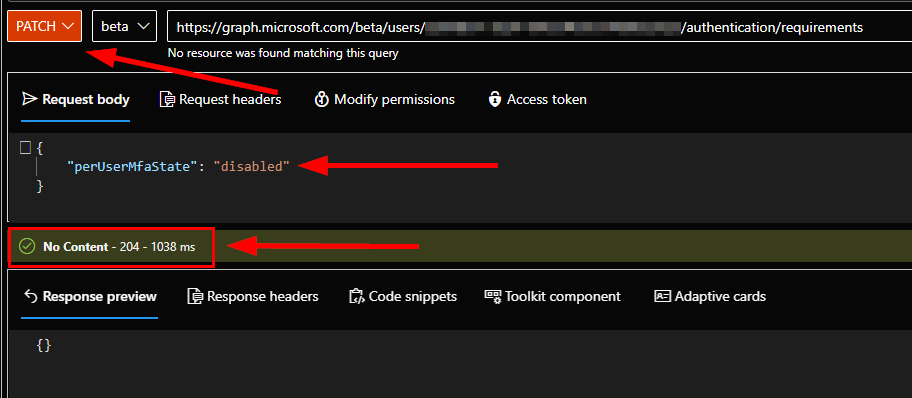
You’re all good if you see a green check mark with no errors in the response. You can then verify by changing the request method back to GET, and we can see the perUserMfaState set to disabled:
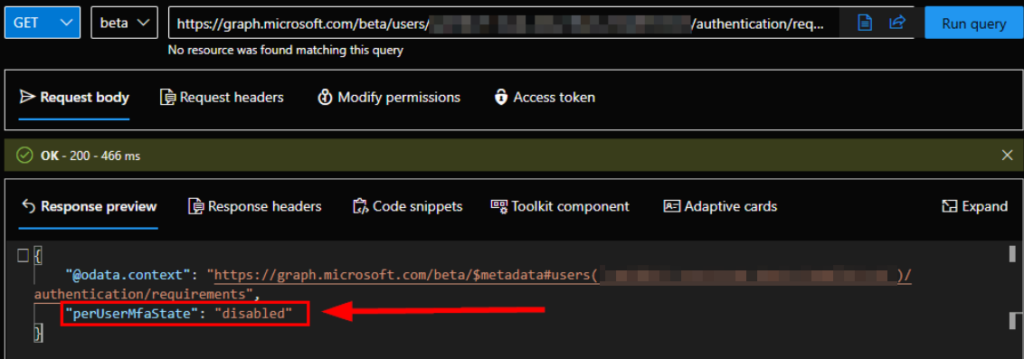
Again, I don’t recommend using Graph Explorer to do this for all users. You should use the script from the post above, which bulk disabled per-user MFA for all users, so your users use conditional access instead of per-user MFA. Now your users should be able to sign into their Entra Joined AVD/W365 devices without issues.