If you’re using Entra Connect and you’re planning to eliminate Active Directory, you’ll eventually need to remove Entra Connect and convert all users to cloud-managed identities. Entra Connect synchronizes your AD identities with Entra, giving the users a cloud identity in addition to their on-prem identity. However, AD remains the source of authority for management. Users and groups synchronized with Entra Connect must be managed in Active Directory, and changes to those accounts get synchronized to Entra. So, when you want to transition your identities to be cloud-managed, you have two options: Convert groups of users over time, or bulk convert all your users.
The easy way to do one-off conversions is to move target users to an OU Entra Connect is not syncing. On the next sync cycle, that user will be deleted in Entra (since it thinks the user was deleted from AD). If you restore the user in Entra, the identity becomes cloud-managed. This method is fine for small groups of users, but if you want to convert all your users in bulk, we can use the steps below.
Before doing these steps, Entra Connect should be removed or the services should be stopped. Hopefully, if you’re doing this, you’re decommissioning your Active Directory soon after. If not, and the Entra Connect services are still running and trying to sync, if directory sync is re-enabled in your tenant, then syncing will resume.
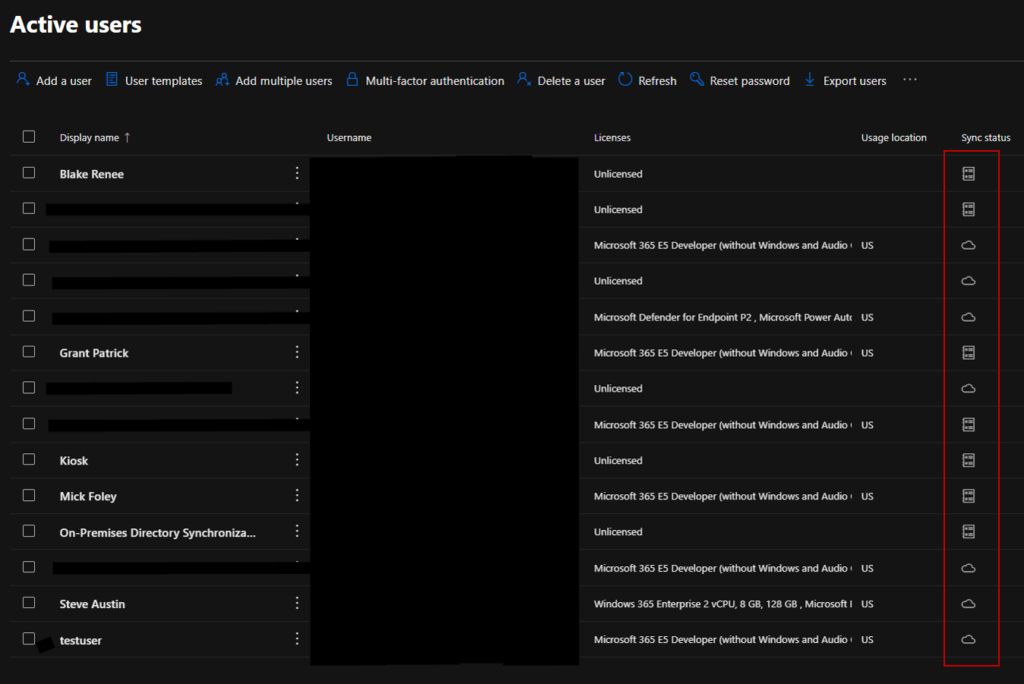
If you’re using Entra Connect, you will have user identities and groups showing synced from AD, like the below screenshot. We want them to have the nice little cloud icon, so they can be fully managed cloud identities.
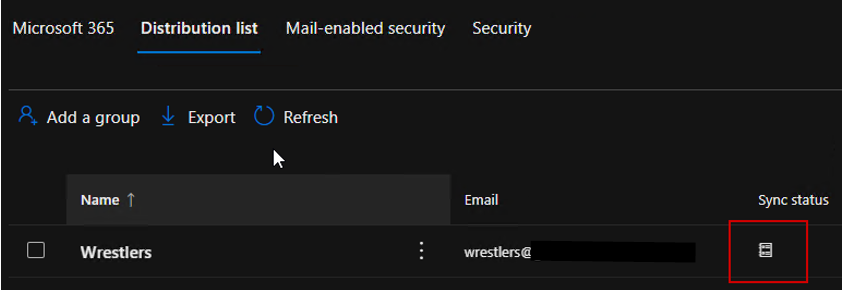
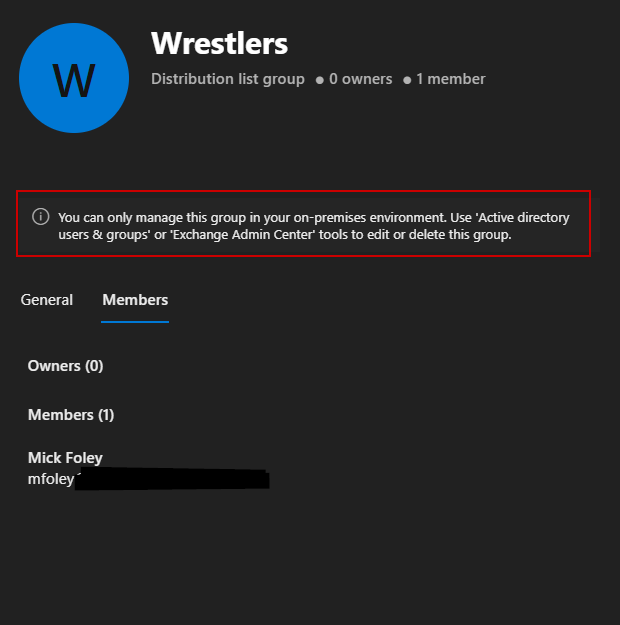
The same management restrictions exist for synchronized distribution and security groups. You can see below that this example synchronized distribution group can only be managed by Active Directory or Exchange. If we want to add a user to this distribution group, we need to do it in AD as long as the group is synchronized.
Converting all synchronized objects to be cloud-managed is rather easy. Open PowerShell and install the MSOnline Module Microsoft Graph Authentication module, then connect to your tenant with Direct
Install-Module Microsoft.Graph.Authentication
Connect-MgGraph -Scopes "Organization.ReadWrite.All"If you try to use the old MSOnline module, you’ll probably get an authentication error since this module is deprecated and not supported in most tenants

We need to disable Directory Synchronization in the tenant to convert all synchronized users to cloud users. We can check the current value of the OnPremisesSyncEnabled property:
Get-MgOrganization | FL *
Setting OnPremisesSyncEnabled to $False will disable directory sync at the tenant level. We can do this with the following command. We need the tenant ID for the update command, so we will first grab that as the $id variable and then pass it in the next command:
$id = Get-MgOrganization | Select -expandproperty ID
Update-MgOrganization -OrganizationId $id -OnPremisesSyncEnabled:$FalseIf we reissue our previous command, now we can see there is a null value for the OnPremisesSyncEnabled property:

This value will likely change to False or be Null right away. However, your users may still show as synced in Entra/M365 for up to 3 days. In my experience, this has usually taken 30 minutes or less, but the official Microsoft documentation states that it can take over 72 hours depending on the size of the tenant.

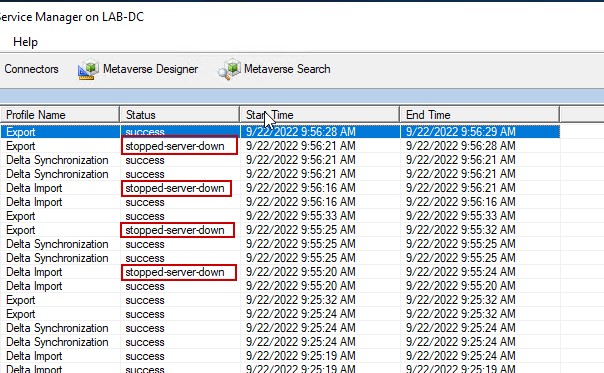
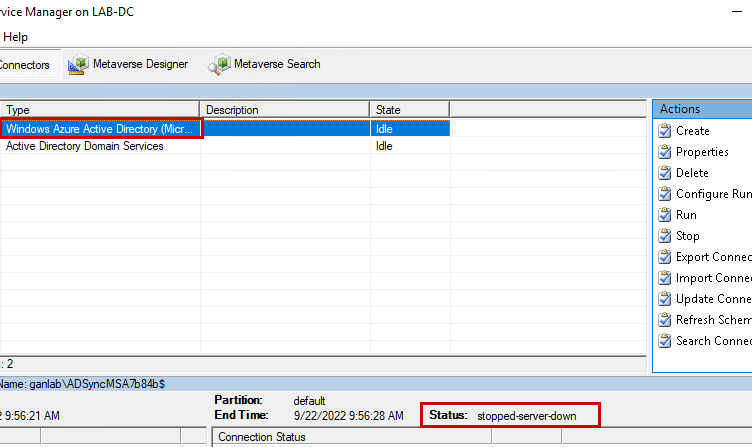
If you still have Entra Connect running, which I don’t recommend, you run a delta sync from the Entra Connect server. It will say success. However, if you open the synchronization service, you’ll see that the Entra Connect server shows stopped-server-down, failing to complete the synchronization tasks. This is why you need to decommission your Entra Connect. If someone mistakenly re-enables DirSync for the tenant, Entra Connect will pick up where it left off and start syncing identities again.
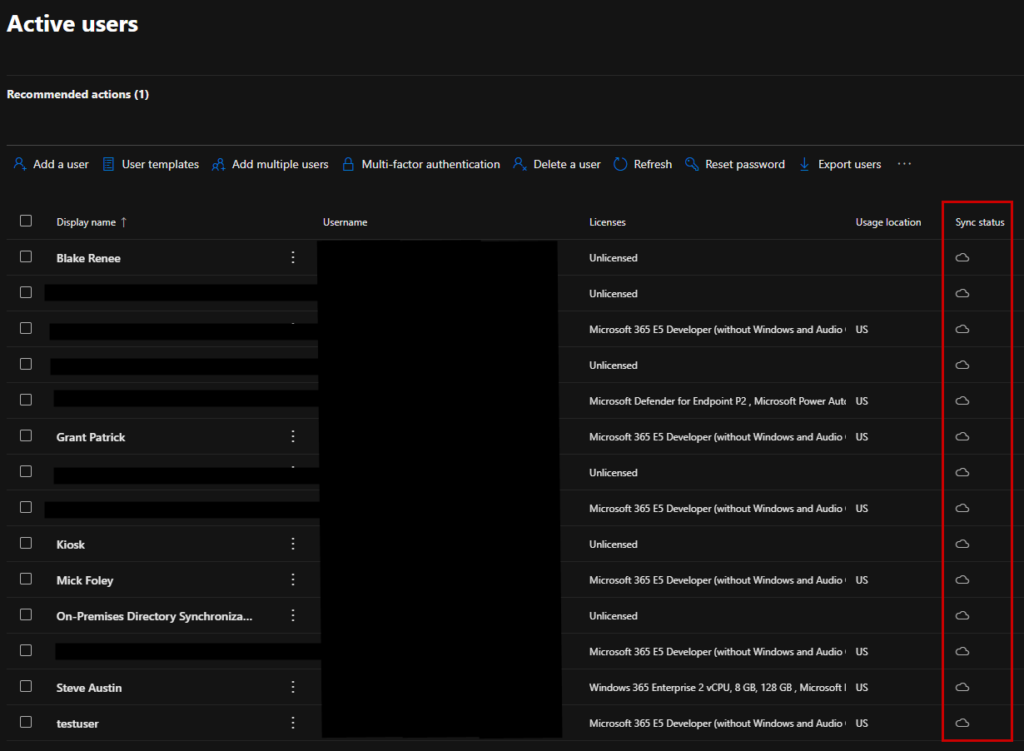
If we return to our M365 admin portal, we can see our users are all cloud-managed. Remember that this may take several hours to several days, but in small tenants, this is usually less than an hour.
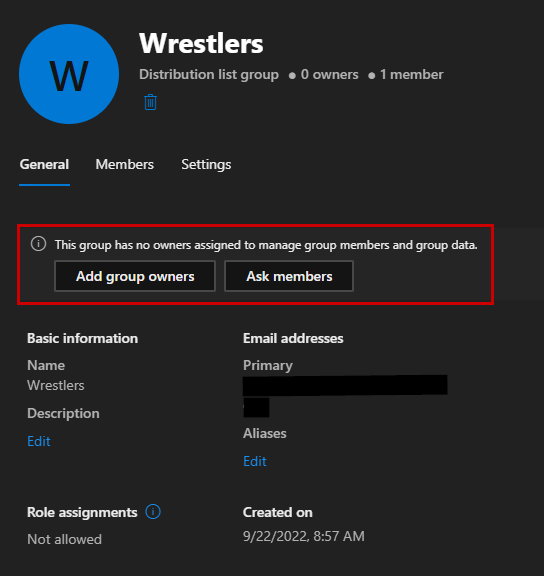
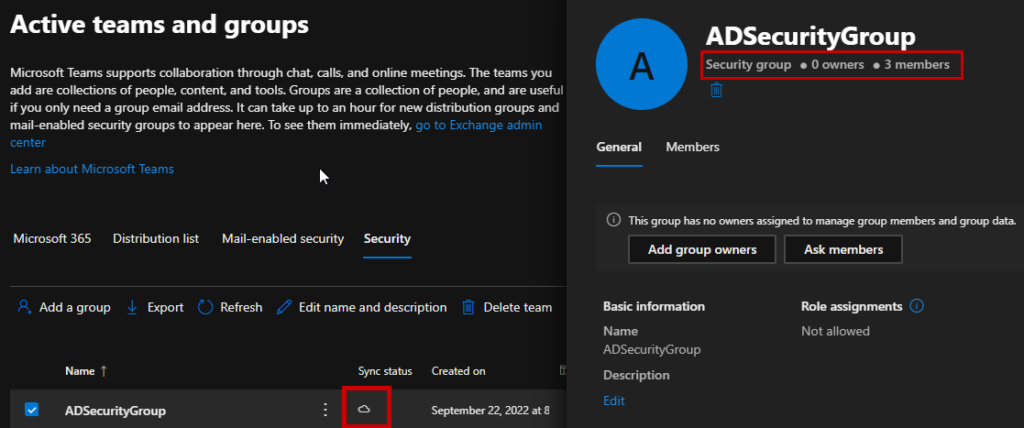
And our Groups are also cloud-managed, while still retaining the members. The Groups will have no group owners, but that’s a minor issue since the members are still retained.
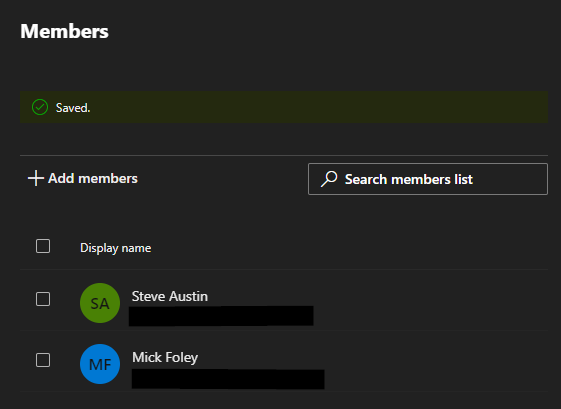
Now that it’s cloud-managed, we can add members.
The same is true for security groups:
Optionally, you can clear the ImmutableID’s from the cloud users who were previously synchronized from Entra Connect The immutable ID is the source anchor that linked the on-prem identity to the cloud identity, (the attribute in AD is the mS-DS-ConsistencyGUID). Clearing the ImmutableID will make it appear as if this cloud was never synchronized with Entra Connect. This does not matter unless the tenant is ever re-synced with Active Directory, which is extremely unlikely, but I will go through it anyway.
First, we need to connect to MgGraph Beta with the proper permissions. At the time of this writing, we can only see the user immutable ID using the beta SDK:
Install-Module Microsoft.Graph.Beta -scope currentuser
connect-mggraph -scopes "user.readwrite.all"Here is an example user created by Entra Connect with a value for ImmutableID. You want to look for the OnPremisesImmutableId value. Users who were created as cloud-native will not have this value
Get-MgBetaUser -userid youruser@smbtothecloud.com | FL *
If we want to grab all users who have this attribute set:
$users = Get-MgBetaUser -All | Where-Object {
$_.OnPremisesImmutableId -ne $null
}
$users
Then we can clear the attribute from all users:
foreach ($user in $users) {
try {
Update-MgBetaUser -UserId $user.Id -OnPremisesImmutableId $null
}
catch {
Write-Warning "Failed clear Immutable ID for $($user.UserPrincipalName): $_"
}
}And then check to make sure its been clear from one of the users:

If for some reason you ever need to re-enable directory sync for the tenant:
Update-MgOrganization -OrganizationId $id -OnPremisesSyncEnabled:$True