If you use Teams as a collaboration tool, you or your clients may have outside businesses they collaborate with. The traditional way to add outside users is to add them as guest users, and then give them permissions to your Teams/Channels. However, what if this is a long term project, you have numerous departments or users from the other organization you’re collaborating with, or perhaps a sister company that has a separate tenancy but you work very closely with on certain things? Enter the Azure B2B direct connect trust relationship. At the moment, this solution is fairly limited, but I anticipate the offerings will expand in the future. The primary benefit of using Azure AD B2B direct connect is you can seamlessly add users from the trusted tenant to a shared Teams Channel, and it appears in their Teams without the need to switch organizations. Before going further, B2B direct connect may not be the best solution for you. This is especially true if the collaborating party is not using AzureAD for their identity management solution. Microsoft highlights the differences of using B2B Direct Connect vs B2B collaboration in Teams here:
- With B2B direct connect, you add the external user to a shared channel within a team. This user can access the resources within the shared channel, but they don’t have access to the entire team or any other resources outside the shared channel. For example, they don’t have access to the Azure AD admin portal. They do, however, have access to My apps portal. B2B direct connect users don’t have a presence in your Azure AD organization, so these users are managed in the Teams client by the shared channel owner.
- With B2B collaboration, you can invite the guest user to a team. The B2B collaboration guest user signs into the resource tenant using the email address that was used to invite them. Their access is determined by the permissions assigned to guest users in the resource tenant. Guest users can’t see or participate in any shared channels in the team.
Let’s take a quick look at setting up Azure AD Direct Connect with two test tenants, how to add users from the trusted tenant to a shared Teams channel, and what the end user experience looks like for the collaborating user.
Creating the B2B direct connect relationship is quick and simple. You’ll need the other tenant ID or domain name (both organizations need to complete these steps). Go to Azure AD > External Identities > Cross-Tenant access setting. From here, click Add Organization and provide the tenant ID or domain name. As mentioned already, the collaborating Azure AD tenant must also complete this step for your organization. In this example, my tenant (ganlab) and another test tenant (1rry0) will be collaborating.
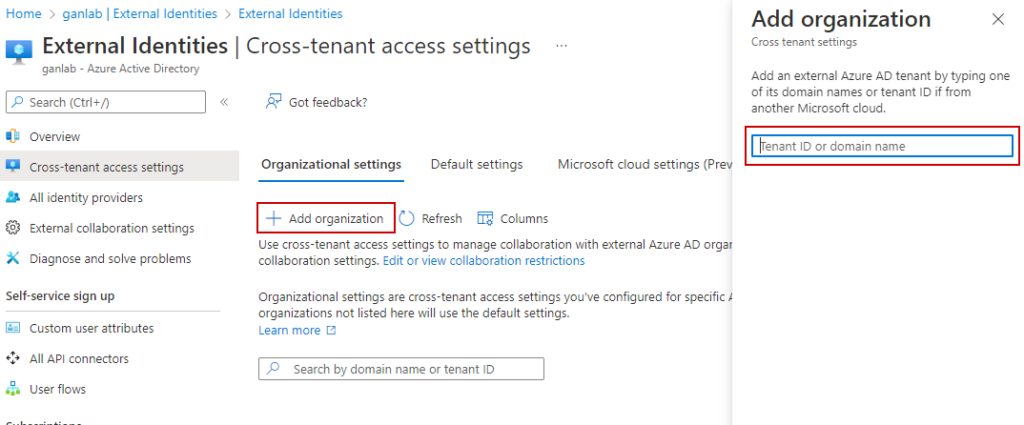
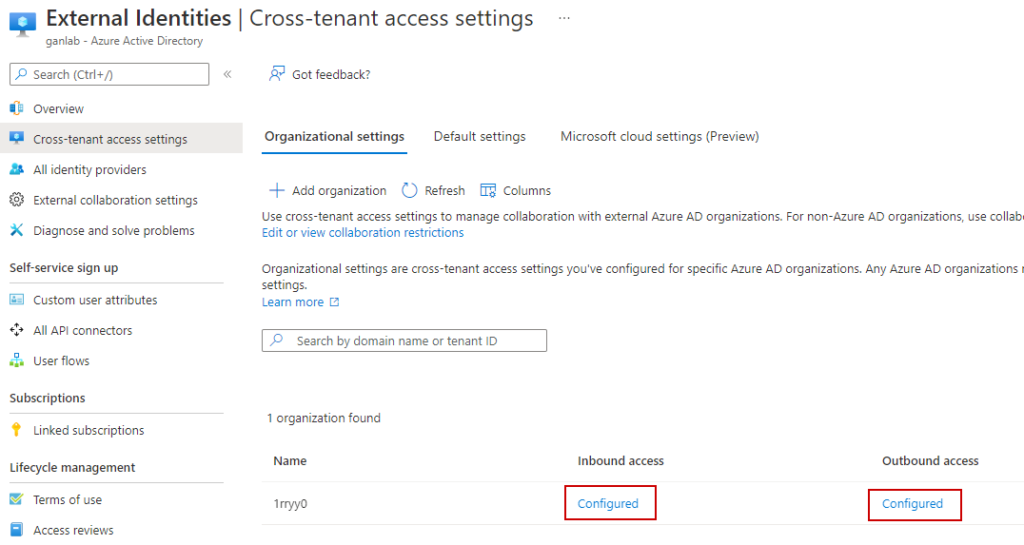
After adding the organization, you need to set permissions. You can limit this to just specific groups or users from the collaborating org if you’d like (note if you do, you’ll need the object ids of the users or groups in the other tenant). In this example, I’m allowing all users & apps. Select the links under inbound access and outbound access (remember, the other tenant also has to complete these steps for your org):
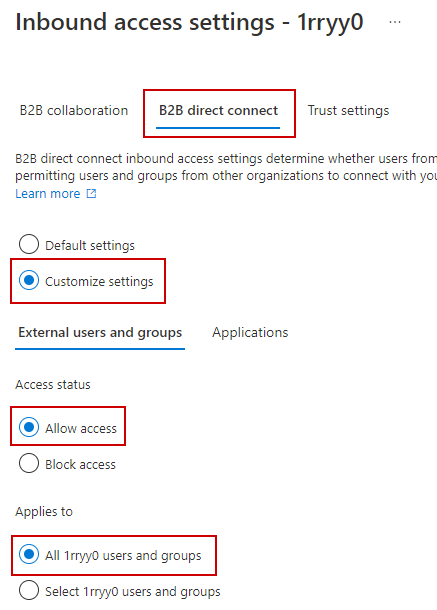
By default, B2B direct connect inherits default settings of block. Change to Customized settings, and edit the access:
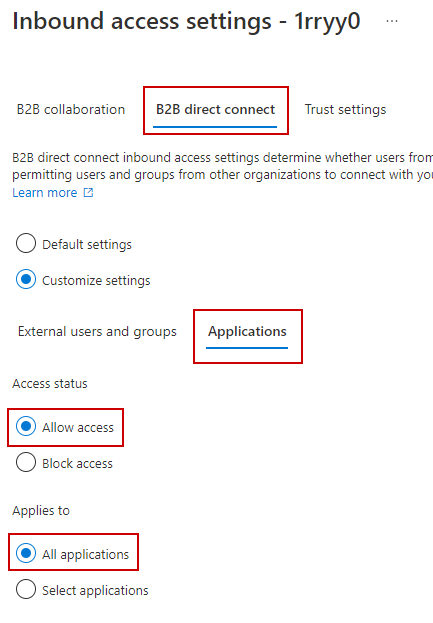
Do the same for the application access:
Lastly, if you’re using conditional access policies in your tenant for MFA, and/or you’re requiring a compliant device for accessing company resources, we need to trust MFA and compliant devices from the other tenant:
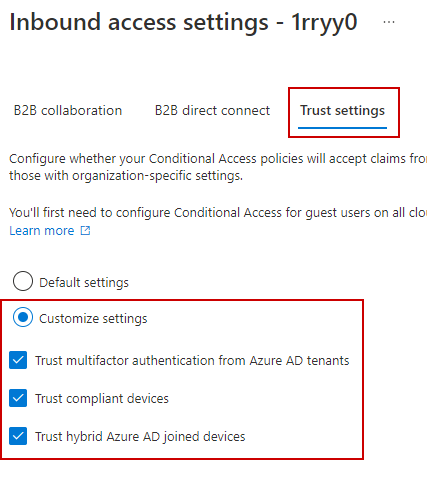
Complete the outbound settings also:
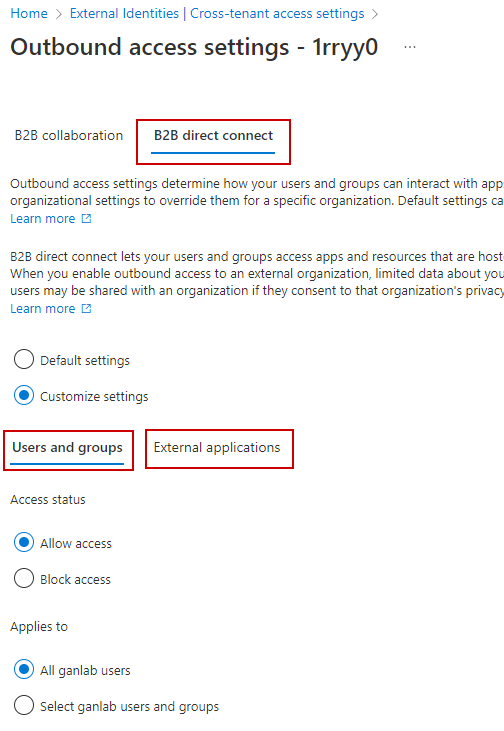
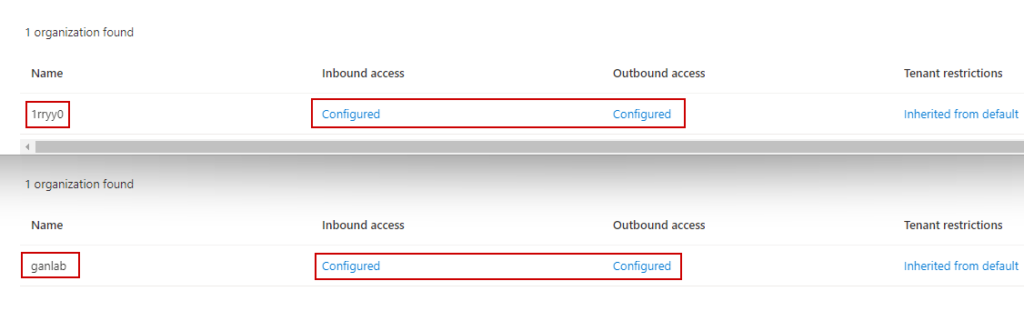
Once your inbound and outbound settings are configured in both tenants, we can try adding users to a shared Teams channel. Here’s a screenshot of both tenants showing the B2B direct connect access settings showing configured:
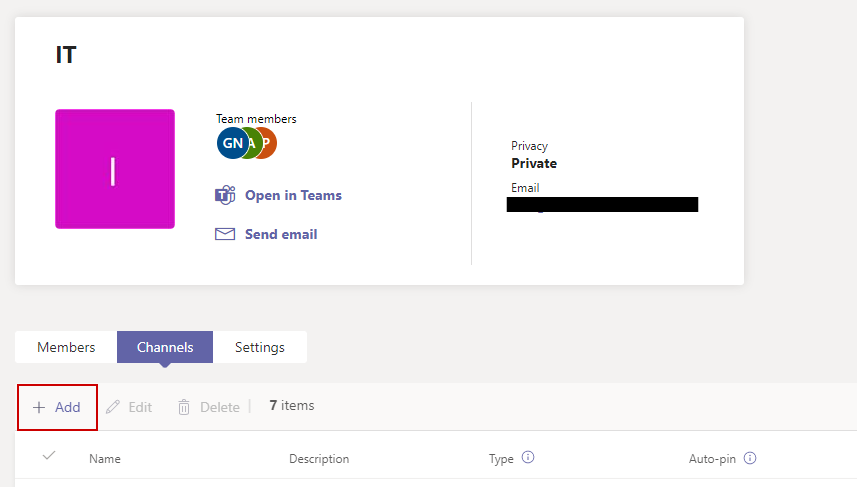
Let’s create the shared channel for collaboration with the trusted organization. I’m doing this in my ganlab tenant. Sign into Teams admin center, find the Team you want to add a shared channel to, and add a channel.
Make sure you select Shared as the channel type, and add at least one owner. Teams admins or channel owners can add users to a shared channel.
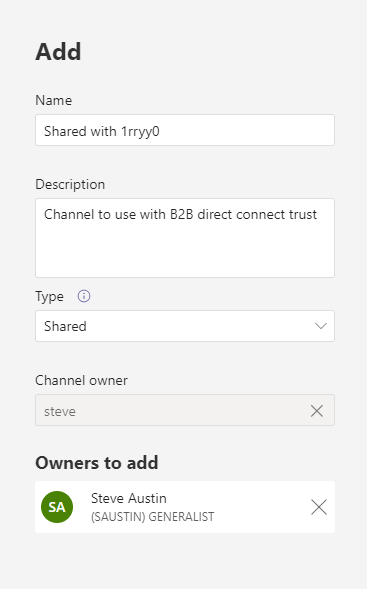
Next, let’s try adding a user from the other organization we set up with B2B direct connect – if users don’t show up right away, you may have to wait. It took around 30 minutes after the B2B direct connect was established before I could add users from the other tenant:
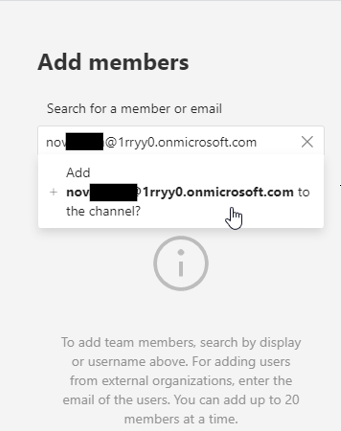
Let’s go back to teams and manage the channel. We can see the external identity from the other organization:
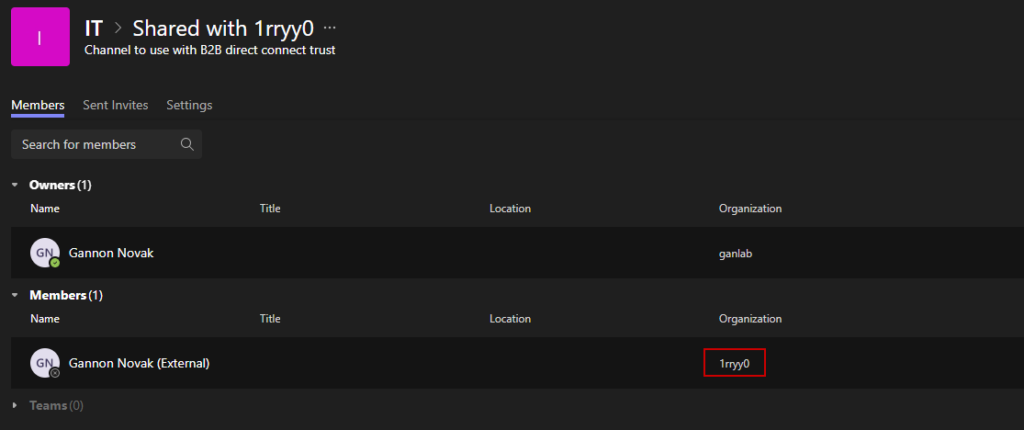
If I sign in with the account from 1rryy0 organization and open Teams. I can see the shared channel from ganlab amongst my native Teams without having to switch organizations. You’ll only see the shared channel. Hopefully in the future Microsoft allows for full Team access:
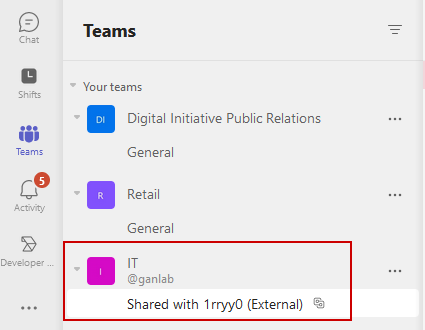
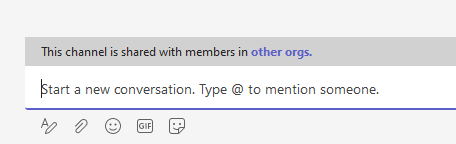
You can see the notification in the chat box that the channel is shared with other orgs:
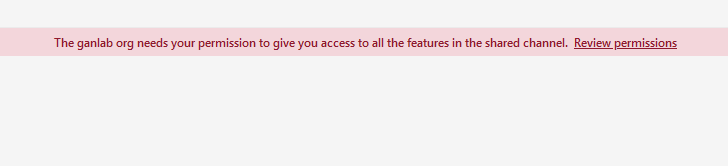
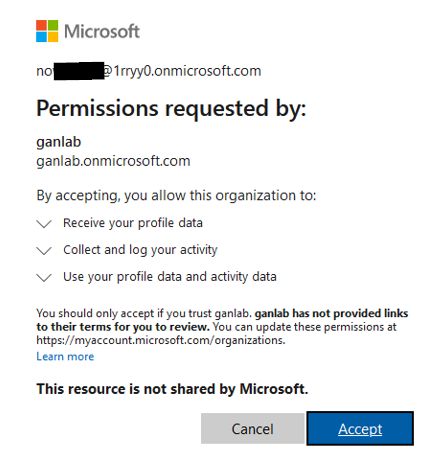
Your collaborating users will have to review and accept the permissions when opening the channel for the first time:
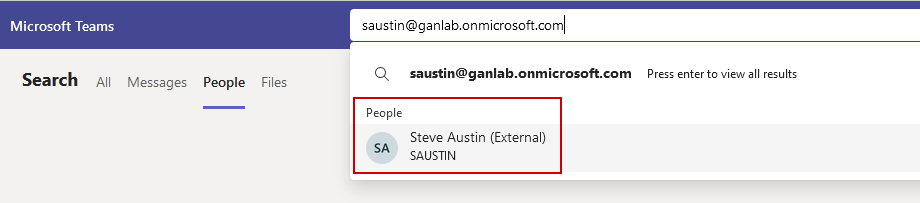
Additionally, you have seamless ability to chat with users from the other organization by searching for them. The top screenshot is the user from the trusted tenant (1rryy0) searching for and chatting with a user in my tenant (ganlab). The below screenshot is me searching for a user in a non-trusted tenant.
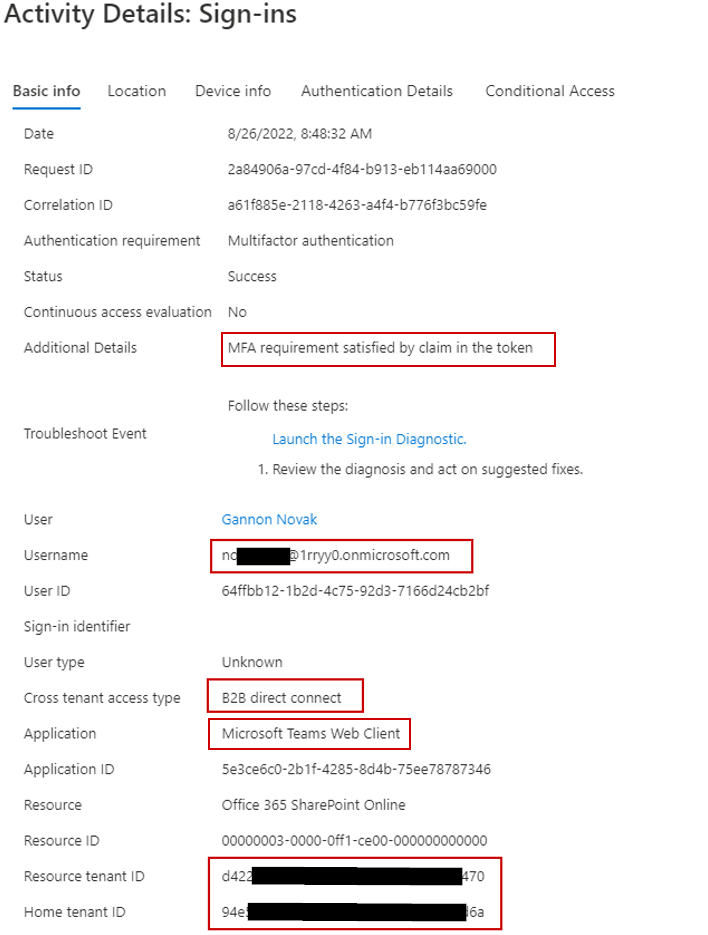
Lastly, let’s look at the sign-in logs on my tenant. This is important to understand – B2B direct connect does not create any user identities for the collaborating users in your Azure AD. Its simply trusting the other tenant. If we look at the sign-in log for the 1rryy0 user on my tenant (ganlab), we see some interesting info. The username shows the full name of the visiting user, shows MFA was satisfied by the other tenant, that the cross-tenant access type was B2B direct connect, and provides the resource and tenant ID’s:
Official Microsoft resources:
