If you work for a CSP/MSP and you use Partner Center to control access to Client environments, this post may help you determine which existing GDAP permissions are out there. We won’t be going into how to request an admin relationship or assign roles to a security group. This post is focused on existing admin relationships and GDAP assignments. For example, if you’re Partner Center is a mess (many of them are), or you started a new position and inherited many existing GDAP relationships, this script will help you determine which roles are assigned to which security groups in your tenant for each client that has an active admin relationship.
To give a very high overview of how GDAP works – it’s essentially giving users from your tenant role-based permissions to a client tenant. This happens based on role assignments on security groups in your tenant. For example, Group A in your tenant may have the User Administrator and Helpdesk Administrator roles in the client tenant, and Group B may have the Intune, Exchange, and Teams administrator roles assigned for the client’s tenant. This is why it’s called GDAP (granular delegated admin privileges). You can granularly assign specific roles to different security groups, so members of your organization have least privilege role access to the client’s tenant. The pre-requisite before roles can be assigned is establishing an Admin Relationship with the client. When an admin relationship is requested, you choose which roles you want to be available to assign to your security groups. The Client can then accept or decline the admin relationship. If they accept it, then you can begin assigning any of the roles that were accepted to your security groups. For specific details on all these steps from start to finish, see this – Granular delegated admin privileges (GDAP) introduction – Partner Center | Microsoft Learn.
Partner Center is sometimes misunderstood and since this is not a very well-known area for some organizations, it can get messy, or have far more permissions assigned to some users than you want. You can see the role-assigned groups for an admin relationship under Partner Center > Customers > Select Customer > Admin Relationships. Here you can see the Name of the admin relationship, the roles that were accepted for the relationship by the client, and the security groups that have roles assigned:
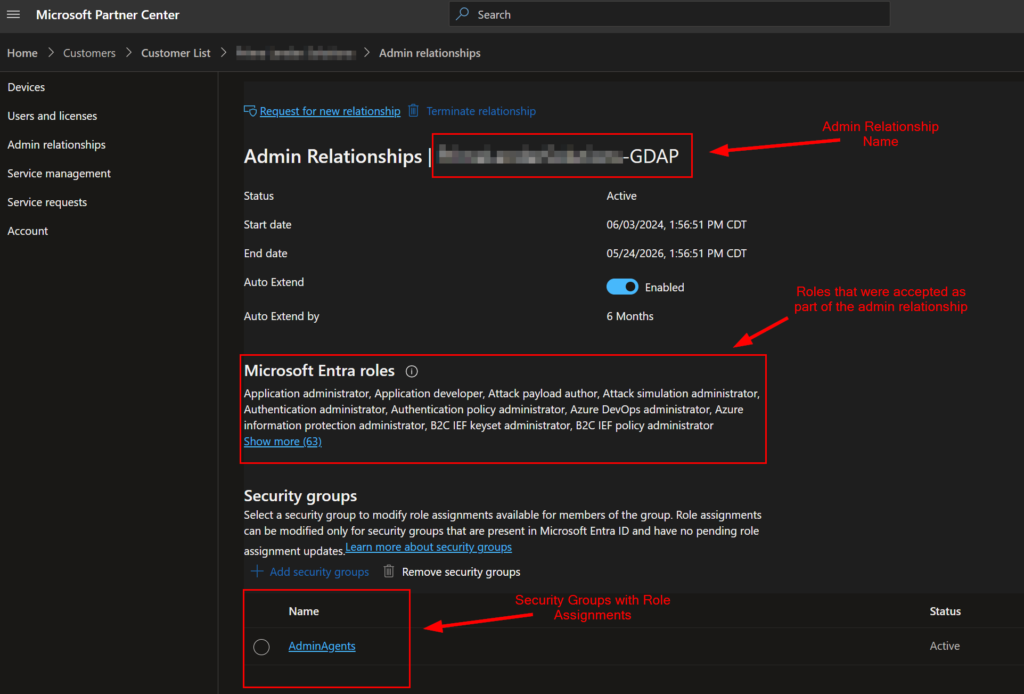
Clicking on the name of the security group will bring up a tab showing all of the currently assigned roles for that group:
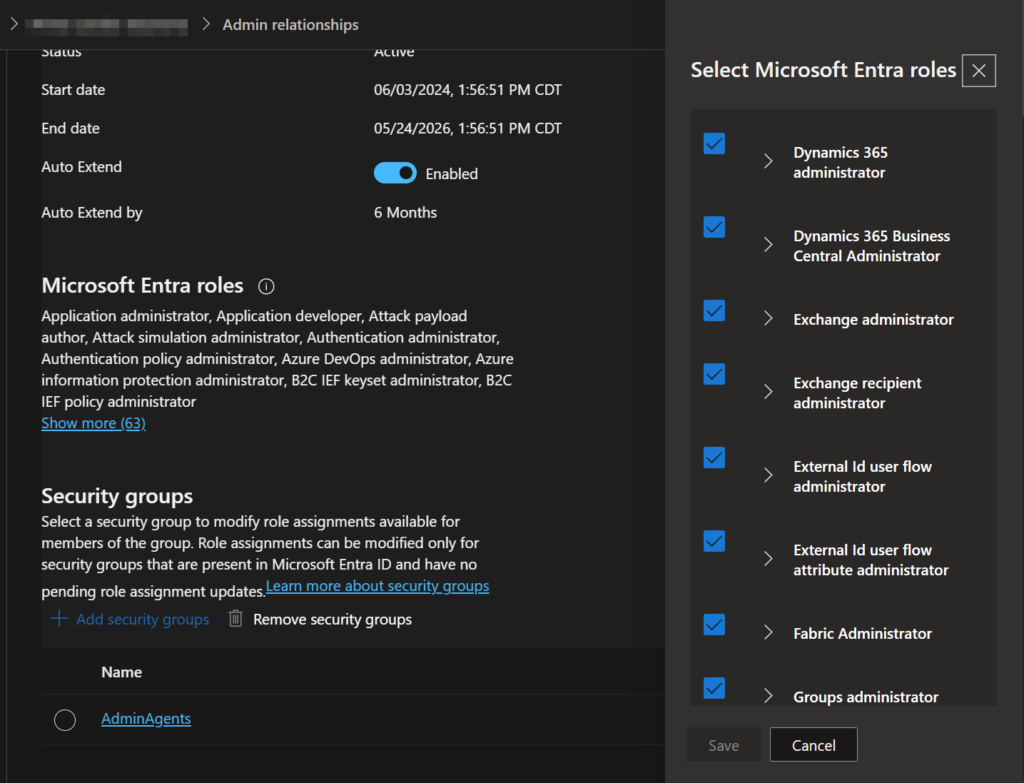
That’s the manual way to check. But, if you have tens or hundreds of clients to look at, this will take forever. Luckily, there is a PowerShell module to help with this – Microsoft.Graph.Identity.Partner Module | Microsoft Learn. This module has some cmdlets that allow you to look at your partner center customers, view admin relationships, and view the permissions assigned to the security groups. For my use, I wanted an export for each customer, the security groups with roles assigned, and which roles were assigned to those security groups. What I came up with is a script that does the following:
- Identifies active client admin relationships in partner center
- Identifies any security groups with roles assigned
- Identifies all roles assigned to each security group
- Exports this data to a spreadsheet.
- The spreadsheet is exported to c:\temp with the name pre-fix “GDAP.Report-” followed by the admin relationship name.
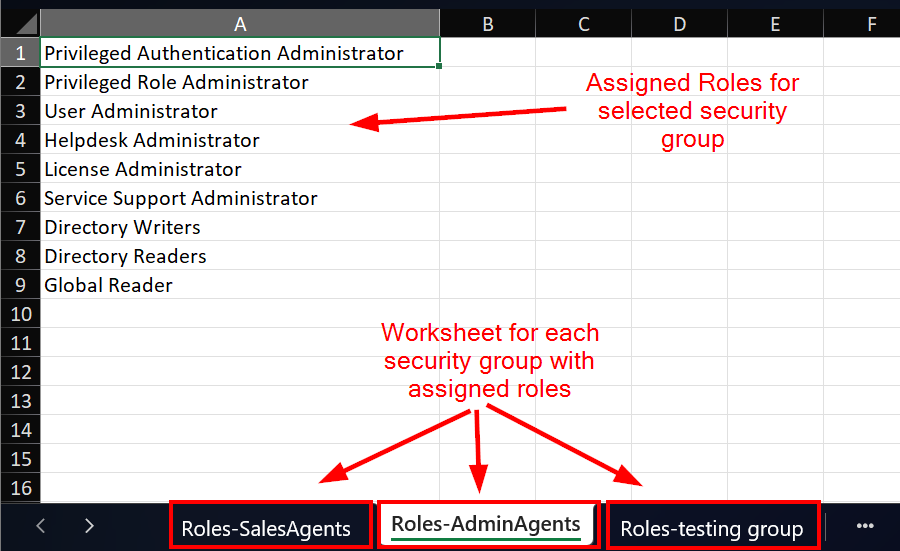
- Each security group will have a worksheet tab with the name of the security group and the role assignments in the spreadsheet.
The script is available on GitHub. Depending on how many clients you have with established partner relationships, the script may take several minutes to complete. Here is an example of it going through a couple of clients:
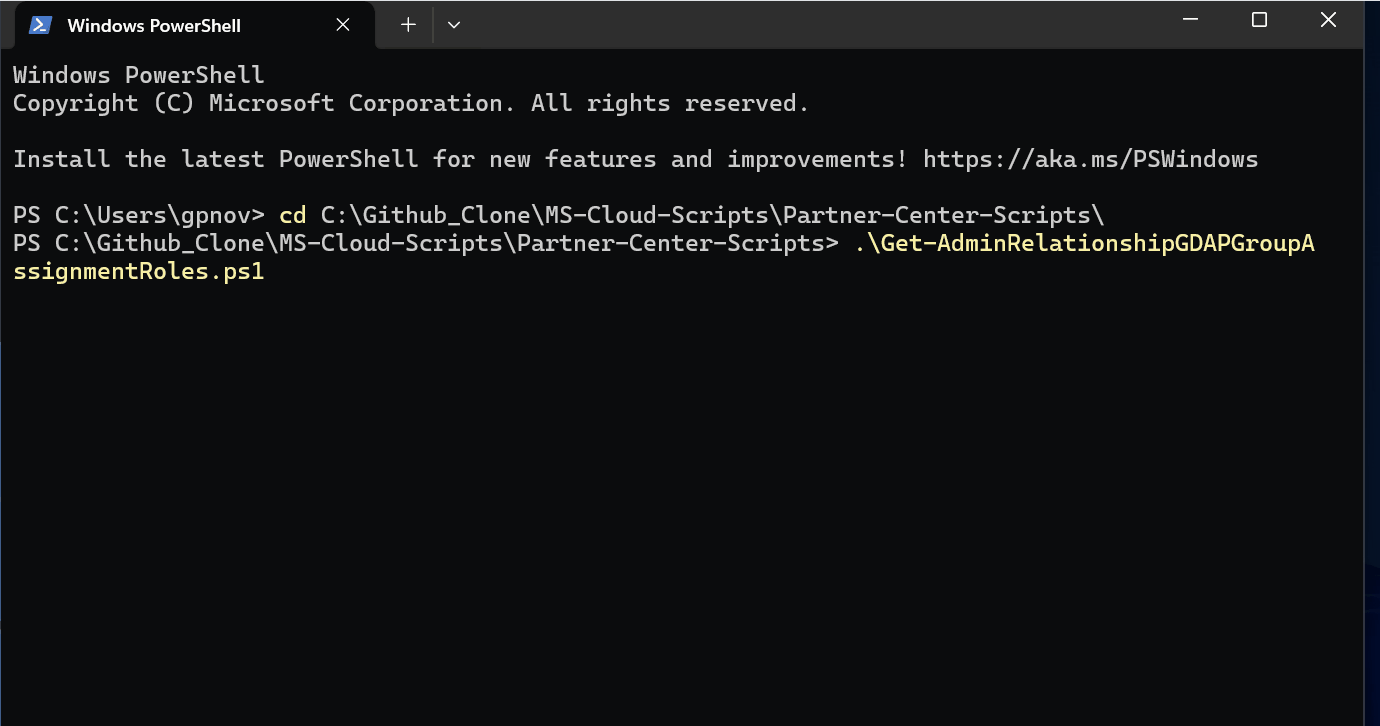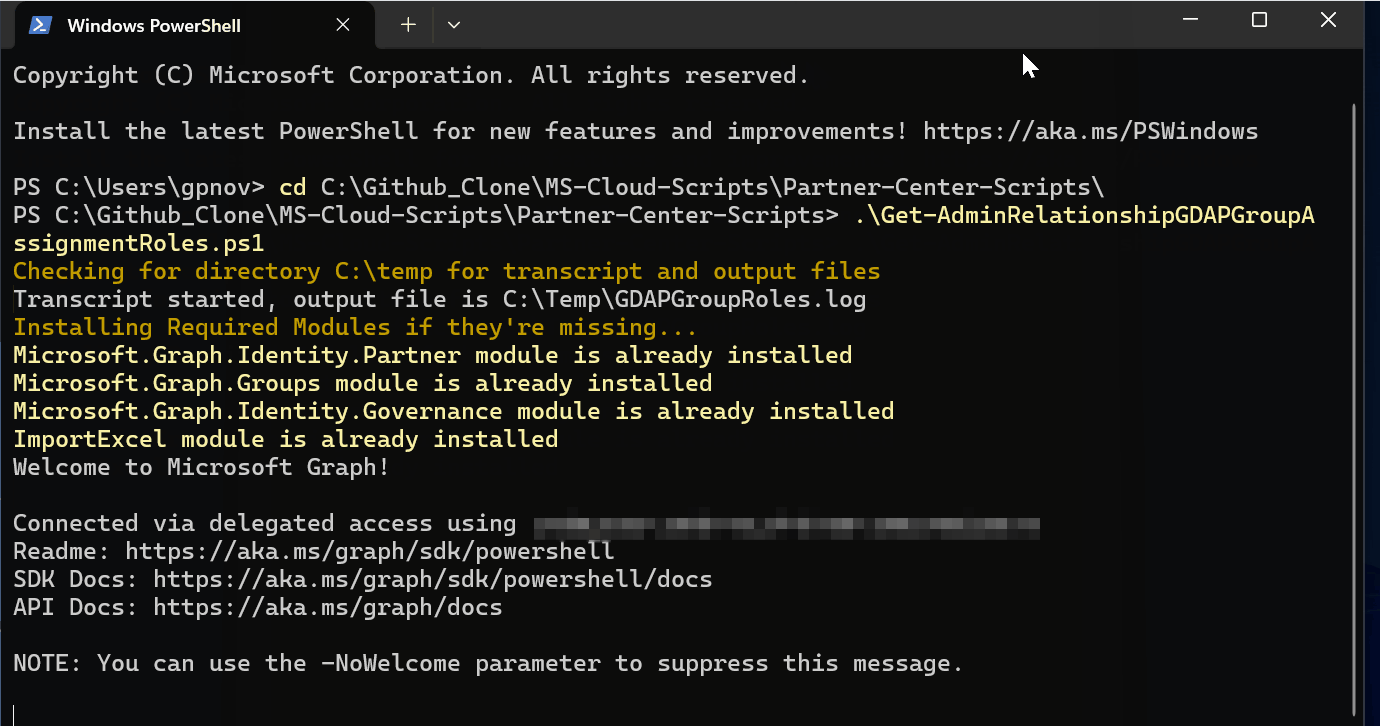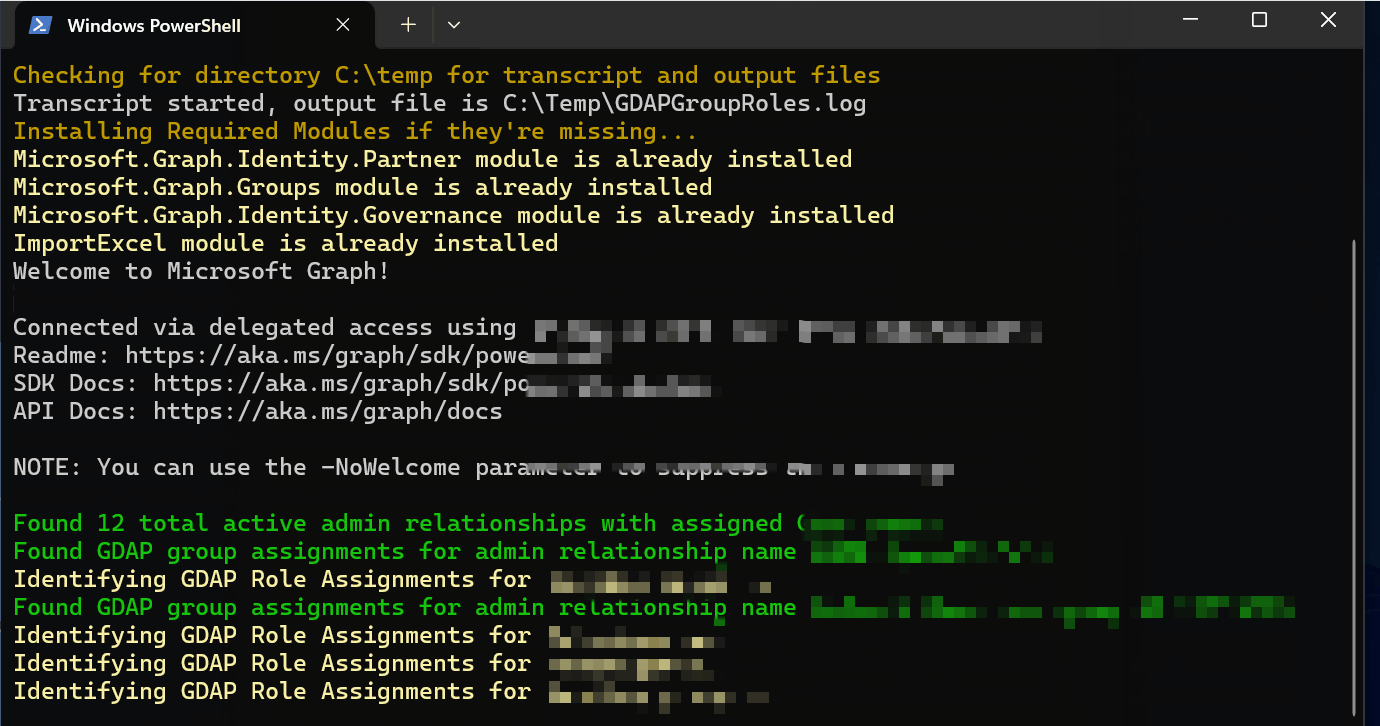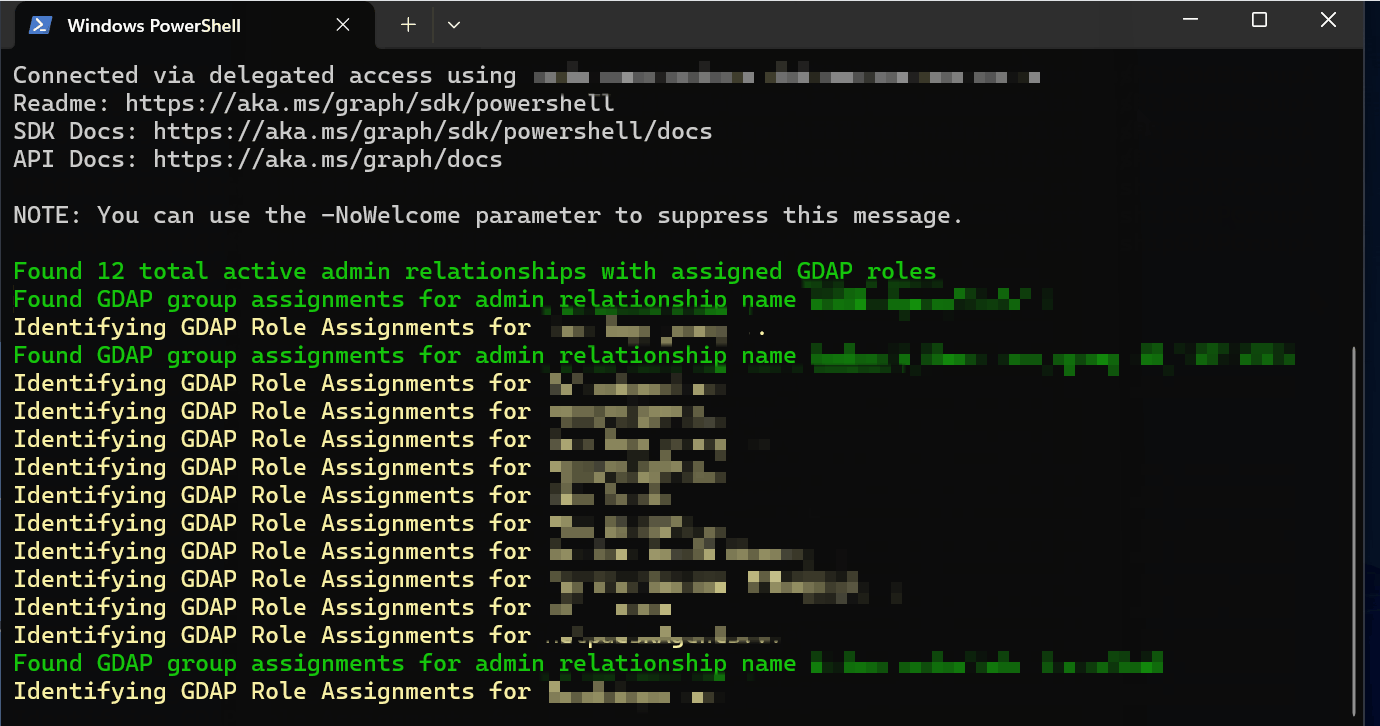
Here’s an example of what the output looks like:
And what the spreadsheet report for each client will look like: