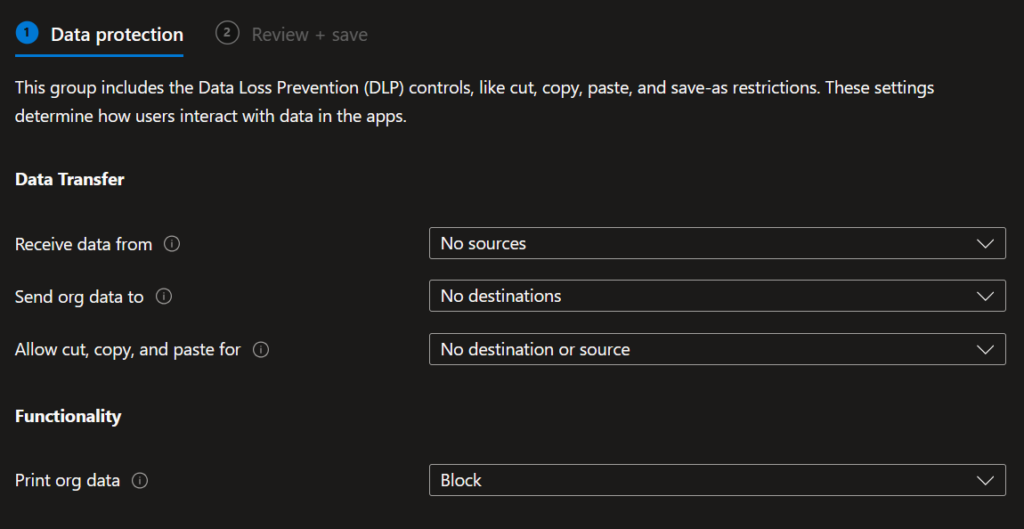
Handling Unmanaged Windows Devices – Using Windows MAM with Intune
All organizations differ in how they want to secure (or not secure) their data. Inevitably, the weakest points in an organization’s defense are the end users and endpoints. Allowing any device access to corporate resources is generally not a good practice. It’s much easier to control access from company-owned hardware since we can ensure our … Continue reading Handling Unmanaged Windows Devices – Using Windows MAM with Intune
1 Comment